
The goal was to create a secure and anonymous communication system for government agencies. Many people use Tor to avoid surveillance by government agencies, ISPs, or other entities monitoring online activities. Similarly, people in countries with strict internet access and usage regulations must use Tor clients or virtual private networks (VPNs) to access some public websites. In this article, we have explored what the dark web is and how Tor Browser provides the necessary anonymity and encryption to access it. We discussed the importance of setting up Tor Browser correctly, ensuring security and anonymity, and navigating the dark web safely.
You can now safely browse dark web websites and hidden wikis, but if you plan to do anything more than that, you’ll need to take several precautions. If you plan to purchase on a dark net marketplace or dark web commerce sites, you’ll need to create a fake identity. Remember only to make purchases using digital currencies and never provide any online banking login details. If you want to be extra safe, routing your connection through a VPN and then accessing the dark web using the Tor browser provides more security than Tor alone. You can also use the Tails operating system to further protect yourself.
Enter A Darknet Web Address
Books, video games, apparel and rare collectibles are some of the legal items you can buy on dark web commerce sites. Samson has over 3 years of experience writing about VPNs for Cloudwards. Apart from his professional endeavors, Samson is passionate about soccer and enjoys reading, table tennis and watching sports in his spare time. He has also contributed to platforms like Financesonline.com and Timeero.com. Don’t open attachments from untrusted sources, as they are a common vector for spreading malware.
Myth 1: The Dark Web Is Only Used For Illegal Activities
Everything you do is protected by NordVPN, which is key to accessing the dark web and enjoying it privately. The entry node encrypts your traffic and it bounces across several nodes in the Tor networks until it reaches the exit node. This node decrypts your traffic and it reaches the destination i.e. the website you want to visit. If you log into personal accounts on the dark web or visit websites with tracking scripts, then your activity may be tracked. Similarly, unless you’re using a VPN, your IP address will be visible to the first relay node you connect to. Tor is a web browser that lets you stay anonymous online or access the dark web.
Examples Of Legal And Useful Dark Web Content
Turn on your VPN and launch the Tor browser and it will automatically connect to the Tor network from which you can access the Dark Web anonymously. On the Dark Web, you will not find search results indexed by Google, which can make it difficult to find what you are searching for. The Tor browser is completely free to use and is available for most major platforms, including Windows, Linux, macOS, and Android. You simply need to download it for the platform you use and install it on your system. While the Tor browser gets updated automatically, you should manually check whether updates are available from time to time. Understanding the Dark Web and its access tools, such as Tor, is crucial for anyone considering exploring these hidden parts of the internet safely and responsibly.
Step 3: Adopt “operational Security”
Therefore, remaining vigilant and practicing caution on the dark web is crucial. The darknet is crawling with criminals; anyone can scam you or make you a victim of phishing attacks. If you don’t remain vigilant and practice caution, many services you curiously investigate might be scams profiting off willing customers. The certified Tor Project advises against this method, making it less common.
Steps To Install Tor
Install the VPN and connect to a server before opening Tor to prevent IP leaks. The nearest server will typically provide the fastest and most stable connection speeds. If you discover your data on the dark web, act quickly to minimize the damage and report the incident to relevant authorities to ensure any necessary legal action is taken. Despite its legitimate uses, cryptocurrency’s untraceable payment nature has raised concerns around money laundering and illicit trade, driving regulatory scrutiny. Bitcoin is the most widely recognized and utilized cryptocurrency on the dark web.
Avoid Downloading Files And Clicking On Suspicious Links

The dark web is made up of a variety of different overlay networks and accounts for somewhere between 5-6% of the overall internet. It allows users to buy and sell, browse, and communicate with nearly complete anonymity. There are a huge number of overlay networks to choose from, but some of the most popular include Tor, Freenet, and Riffle. You’ll need an overlay network to facilitate your dark web access.
The dark web is home to plenty of unlawful activity, so you must ensure you never get involved in something illegal. Internet traffic is secured using adjustable levels of encryption. You can choose 256-bit for maximum protection or 128-bit if you want a faster connection. There are multiple protocol options available and protection against IPv6 leaks and DNS leaks. Accessing the dark web is not illegal in the United States, but naturally, engaging in illegal activity while on the dark web can get you in hot water. For example, last June, two men were charged by the federal government for operating the Empire Market, which was a dark web marketplace where people could buy and sell illegal items and services.

What Are The Best Privacy Tools For The Dark Web?
Many sites become defunct quickly, either because they are shut down due to illegal activity, their founders lose interest, or they change addresses and names to avoid detection. Next, select a dark web search engine like DuckDuckGo that can help you find dark web websites that cannot be indexed by traditional surface web search engines, such as Google or Bing. Many dark internet users favor Tor which uses a network architecture originally developed by the U.S. Naval Research Lab as a system of decentralized, anonymous nodes to enable anonymous online communication.
- Freenet is easy to set up because you simply need to download, install, and run it.
- Unlike Tor, however, it cannot be used to access the public internet.
- Users can mix their digital currencies to break the connection between the sender and the receiver.
- Search engine results from Google, Bing, and Yahoo, public websites, social media, and anything else that’s indexed and publicly available is considered a part of the surface web.
- Others were casual users—people buying fake IDs, stolen credit card numbers, or drugs.
Tor protects your identity inside its network, but it doesn’t hide everything. Your ISP still knows you’re using Tor, and entry nodes can see your real IP address. A VPN adds protection before Tor, closing these gaps without breaking access to .onion sites. By following these guidelines, you can safely explore the dark web and its plethora of .onion sites, unlocking a world where privacy and freedom are at the forefront. Remember, while the dark web offers a unique environment for secure browsing, it is always essential to navigate it with caution and awareness.
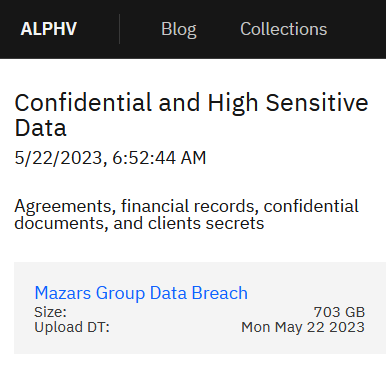
The deep web is crucial for maintaining privacy and security online, as it keeps sensitive information away from the prying eyes of the public and search engines. While the term “deep web” might evoke images of hidden, secretive content, most of it is just routine data stored on private networks. The surface web is the part of the internet most of us interact with daily.



