This website allows you to type in your email address or phone number and see if it’s been compromised in any data breaches. If your information has been compromised, then it’s likely that your phone number is also on the dark web. One of the great things about Tor is that it can be used to access both the dark and surface web. Just note that although you’ll be anonymous, you won’t have the speed or convenience of a direct connection, and some sites might block you outright. For a number of technical reasons, it’s much faster and more reliable than Tor. The peer-to-peer routing structure is more advanced, and it does not rely on a trusted directory to get route information.
Choose A Dark Web-compatible Search Engine
If you’d like to use it to exchange currencies, please feel free. Hacking and cybercrime forums on the dark web are spaces for newbie hackers to ask questions, veteran cybercriminals to share their expertise, and buyers to find sellers. Cybercrime services are more commonly sold through marketplaces, but you can usually find someone offering hacked servers, computer logins, and stolen data on such forums. Encrypted communication channels on the dark web allow users to message back and forth in an anonymous online environment. However, some surface web platforms like ProtonMail offer encrypted email services in addition to dark web versions that enable people residing in more repressive areas to communicate freely.
Types Of Dark Web Websites

It enables you to navigate through the Tor network, which anonymizes your online activity by bouncing your connection between multiple relays. Download and install the official Tor browser from the official website to ensure security and authenticity. Dark markets continually adapt and evolve to stay ahead of law enforcement and security measures. As one marketplace is taken down, another often rises in its place. This ongoing cat-and-mouse game poses a significant technical challenge in combating the activities within darknets.
Illegal Pornography
- In repressive regimes, darknets play a vital role in enabling free speech and access to uncensored information.
- It uses PGP encryption, two-factor authentication, and OPTP authentication to ensure users’ security.
- There are three ways to reach and explore the dark web’s black markets.
- It is a specific Debian-based version of Linux software that leaves no traces of the user activity or the operating system on the computer.
- These documents can be used for identity theft, fraud, or illegal activities.
- In his spare time, Michael likes writing fiction, reading murder mystery novels, and spending time with his family.
Combined with smart surfing behaviour and technologies like Tor and a VPN, even the darkest reaches of the internet may be securely traversed. We respect your privacy and never track or record any details of your online activity. So, be sure that whatever you do on the Internet—browsing, downloading, and other habits — remains completely confidential.

What Services And Tools Are Available On The Dark Web?
That also is why I didn’t share links to darknet markets directly. Taking part in any activity on any darknet market, both legal and illegal, will solely and exclusively be your own responsibility. Contrary to popular belief, accessing darknet markets isn’t “hacker stuff”. It’s just as easy as accessing a social media or e-mail account that you’re familiar with.
- Users slip into this shadowy realm using a anonymizing browser, like Tor (The Onion Ring) browser, and a Virtual Private Network (VPN) to protect their identity and secure their connection.
- Users can find a variety of firearms, ammunition, knives, and other weapons, often sold by anonymous vendors.
- While using a dark web link or dark web onion link may provide a certain level of anonymity, it is not foolproof.
- It doesn’t use JavaScript, meaning the website won’t track your activities or exploit vulnerabilities.
- Tails always starts with a clean slate and any evidence of the activities you engage in while using Tails disappears when you shut down Tails.
- However, it’s much harder to get at the people who are doing the uploading and downloading.
Is The Dark Web Actually Anonymous?

However, engaging in any illegal activities, such as buying illicit goods, remains against the law, just as it is on the surface web. Genesis is currently a by-invitation marketplace, and the user experience on the platform is quite smooth. With a significant growth in the number of bots, as well as the range of accounts that a hackers can target, the popularity of Genesis is bound to grow. It is imperative for cyber defense teams to understand the looming threat of stolen fingerprints. Once a customer purchases a bot, Genesis Marketplace also makes it easy for them to use those stolen profiles.
Alternative Anonymous Networks
Although, more than the “accessibility”, Tor’s security and anonymity are what it’s loved for. This will help you avoid the law, blackmailers, honeypots, bad exit nodes and a lot more. By encrypting communication before it gets to the Tor network, pairing Tor with a VPN gives a second degree of protection. VeePN offers a 30-day money-back guarantee to test all the features for yourself without any risks. With VeePN, you can create a disposable email and get all messages sent to this genuine inbox.
Secure Drop
It’s designed as an environment to elude detection, where site owners and visitors hide their identities. And while the dark web isn’t synonymous with illicit activities, it’s undeniably the breeding ground for the internet’s black markets, hacker forums, malware vendors, and other illegal activity. There are some things that you can’t find on the surface internet but are available in the darknet markets. Therefore, it’s almost impossible for authorities to track those who run the darknet markets or even their locations. It’s legal to access the dark web in the U.S. and most other countries. By some estimates, well over half of dark web content is illegal.
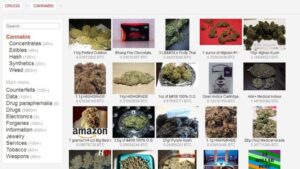
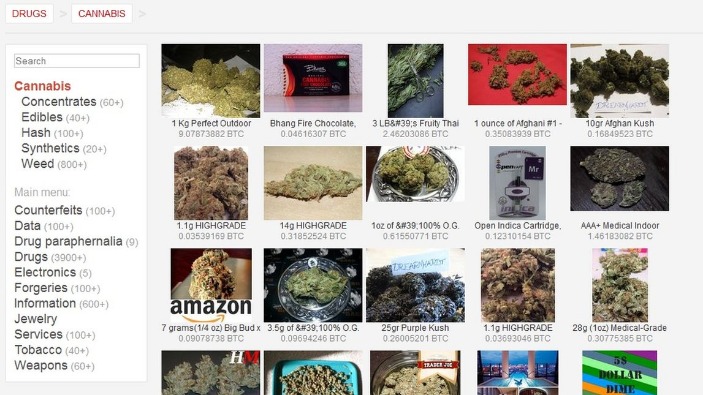
Illegal Drugs
Setting up I2P requires more configuration on the user’s part than Tor. I2P must be downloaded and installed, after which configuration is done through the router console. Then individual applications must each be separately configured to work with I2P. You’ll need to configure your browser’s proxy settings to use the correct port on a web browser. For built-in Tor over VPN functionality, NordVPN operates specialized servers that automatically route you through the Tor network. You don’t even need to use Tor Browser, but keep in mind other browsers can still pass identifying information through the network.
Cryptocurrency Transactions

The technology behind the darknet is actively maintained and continues to evolve. Dark markets often employ end-to-end encryption for communication between buyers and sellers, enhancing security and privacy. This encryption ensures that messages cannot be intercepted and read by third parties, including law enforcement. The use of digital signatures can also help verify the authenticity of users and transactions.
Once installed, users can access darknet markets by entering the appropriate URL into the Tor browser’s address bar. Another risk is the potential for law enforcement and government surveillance. While using a dark web link or dark web onion link may provide a certain level of anonymity, it is not foolproof. The authorities have been known to monitor and track illegal activities on the dark web, leading to arrests and prosecutions.
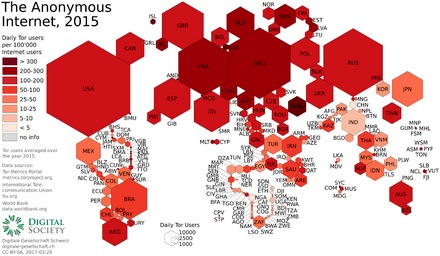
But lurking beneath lies the expansive, mysterious “deep web” or“dark net” – the gigantic submerged part that remains invisible to standard searches. Other dark web search engines worth investigating are Ahmia, Torch, NotEvil, and the Onion URL Directory—just type out some keywords for what you’re looking for. Some of these sites can be found through regular web browsers, but you’ll then need to switch over to Tor once you’ve got the onion links you want to follow. All resources are offered to give insight into the workings of the Tor network and darknet markets.
The platform is also used by governmental cyber departments to identify and track potential criminals or offenders. You can never be sure who’s really behind the other end of the line. But remember, it’s essential to take all the necessary and important security steps before entering such sites on the dark web. As mentioned before, your ISP and government institutions are not able to see what sites you visit on the Tor network, but they can probably see that you use Tor. The last thing you need to do is to start researching vendors and determine what marketplace is a possible vendor to buy the products from.