
I2P must be downloaded and installed, after which configuration is done through the router console. Then individual applications must each be separately configured to work with I2P. You’ll need to configure your browser’s proxy settings to use the correct port on a web browser. For built-in Tor over VPN functionality, NordVPN operates specialized servers that automatically route you through the Tor network. You don’t even need to use Tor Browser, but keep in mind other browsers can still pass identifying information through the network. Alternatively, there’s IPVanish who claim to be the world’s number one VPN for Tor and comes highly recommended, you can save 60% on the annual plan here.
Before diving into the world of the Dark Web, it’s crucial to address the legality and safety concerns. While the Dark Web itself is not illegal, it does provide a platform for illegal activities to take place. Additionally, navigating the Dark Web comes with inherent security risks, as malicious actors may be lurking, attempting to compromise your privacy and steal sensitive information. The dark web is a portion of the internet that isn’t indexed by traditional search engines. It is home to various illegal activities, but it also serves legitimate purposes for privacy advocates and activists in oppressive regimes.
Cybersecurity Student → Conducts research on privacy tools → Accesses ethical hacking forums (legal) using Tor. Journalist in India → Uses Tor to access a whistleblowing portal → Submits information anonymously while protecting their identity. All you need to do is connect to one of Proton’s Tor-enabled VPN servers, and you’re good to go. This method works across devices, meaning you can do this on Windows, macOS, Linux, Android, iOS, and every other device that Proton VPN supports. Download our free MakeUseOf deep and dark web PDF guide, and check out the best dark web websites. These are, however, all issues that the Tor Project will fix over time.
- For built-in Tor over VPN functionality, NordVPN operates specialized servers that automatically route you through the Tor network.
- Some consider VPN over Tor more secure because it maintains anonymity throughout the entire process (assuming you pay for your VPN anonymously).
- You can also use its .onion link via the Tor network to access the site in restrictive countries, where it might be unavailable.
- To navigate the Dark Web, ExpressVPN is the very best choice, with over 3,000 of the fastest servers located in more than 94 countries around the globe.
- It’s a relatively easy process that still maintains a high security level.
With Tor, you can browse the dark web anonymously, without revealing your IP address or location. When browsing the dark web, it is essential to use encryption to protect your online activity, mask your IP address, and safeguard against malware. The deep web is mostly considered as a hub of illegal activities with an accumulation of 15 petabytes of data. Sometimes it often serves as a useful resource for many, while holding power to destroy the personal life of a User as well.
Finance Solutions Provider Systems East Suffers 200k+ Data Breach
Then there’s the less popular VPN over Tor, which is advised against by the official Tor Project. Only two VPN providers that we know of, AirVPN and BolehVPN, offer this service, although neither of these score highly for speeds. Internet traffic first passes through the Tor Network, and then through the VPN. This means the VPN provider doesn’t see your real IP address and the VPN protects you from those bad exit nodes. You can access the dark web on mobile with a dedicated dark web browser app.
One of its selling points is that even ZeroBin servers don’t know what you pasted. The data encryption takes place on your browser before it goes to the server. Staying safe on the dark web requires even more vigilance than the public internet. Scammers and criminals are lurking everywhere to take advantage of the unwary. Follow the pointers below to avoid becoming a victim if accessing the dark web.
Access The Dark Web Safely
Believe me – there are plenty to go around and each and every one of them are being kept under surveillance. Not to mention the fact that you’ll get exposed to some stuff that will definitely make you take several cold showers. Chill, because nobody will ever find a record of you ever fiddling around the darknet. Note that Tails’ installation package is the .img format, which means that you’ll need software capable of burning images on your thumb drive. This multi-layered redirection ensures your actions leave no trace, offering a high level of anonymity. I am Sebastián Vidal, a computer engineer passionate about technology and DIY.
VPNs For Netflix That Actually Work: Unlock Any Series
Just replace the “.onion” suffix with “.onion.pet,” and you should be able to access onion sites in your browser. The free plan comes with Tor-friendly servers in the US, the Netherlands, Romania, Poland, and Japan. This makes it hard to connect to nearby servers, so you might experience noticeable slowdowns — luckily, you get access to VPN Accelerator, which can boost speeds on distant servers. That’s because the provider has advanced features like RAM-only servers, perfect forward secrecy.
Can I Access Dark Web Links Without Using A VPN?
The primary purpose of accessing the dark web is anonymous browsing for activists and whistleblowers, but some people misuse this anonymity for illegal reasons. It is where the dark web becomes dangerous, and with no regulations, it becomes riskier to access without using a protective tool. The cybercriminals are scattered like landmines all around the dark web. Also, ISPs and government agencies monitor your network and track down IP addresses used to access the dark web.
Limit Tracking On The Tor Browser

There a bunch of precautions you can take to further ensure an anonymous browsing experience. The Tor project lists a few of the best practices to follow while using it. The Snappening, a 2014 scandal in which Snapchat users’ private photos were put online, was first posted on Dark Web websites. And the film “Citizenfour” documented how filmmaker Laura Poitras, journalist Glenn Greenwald, and whistleblower Edward Snowden communicated using online Dark Web-esque tools. Even if you are not a customer of illegal marketplaces, visiting them can get you on a government watchlist.
Step 5: Navigating Dark Web Safely
Although the dark web has a reputation as a place full of illegal activities, it also has applications in legal ventures. It is a complex and fascinating part of the internet that is worth learning more about. Virtualization apps will dedicate a portion of a computer’s resources to simulating a separate device. The word “separate” is key here, as this isolation from your “real device” will protect the latter in case anything goes wrong.
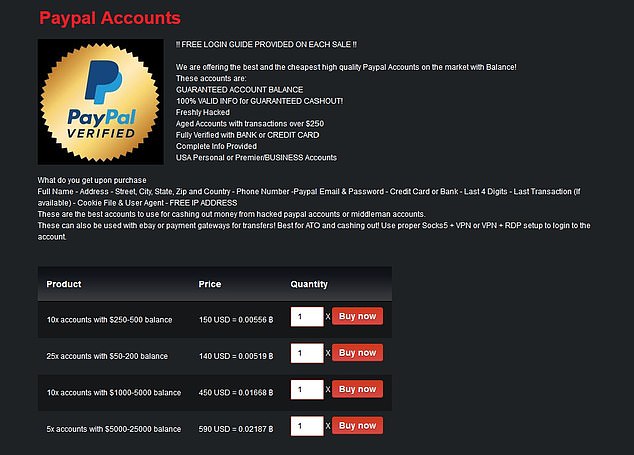
To connect to the Tor network, simply open the Tor browser and wait for it to connect. This may take a few minutes, as the browser needs to establish a secure connection to the Tor network. If you want to access the dark web, your first step toward a more private experience should be to secure your internet connection and data with a reliable VPN. All v3 .onion addresses (the current standard) are 56 characters long and end with “d” to denote the URL version in use. Each address also contains cryptographic information that enables a dark web browser to connect to the site.
- Your ISP only sees the encrypted VPN traffic and won’t know you’re on Tor.
- Exploring the Dark Web on an Android phone can be an intriguing and potentially risky endeavor.
- Yes, there are other tools like I2P and Freenet, but Tor remains the most widely used for accessing dark web content.
- The dark web is the perfect avenue for communicating and publishing sensitive information with no fear of retribution, such as imprisonment.
- Many experts advise against using third-party mobile browsers that utilize the Tor Network.
Step #2: Download The TOR Browser
But it’s also connected to Tor, which means you can now access Dark Web websites and have relatively more online privacy than before. The Dark Web was created by online activists who were trying to share content using the most private methods. Without a doubt, there are a bunch of places in this bizarre grove of the web that people should avoid at all costs. The Tor browser is notorious for providing a secure browsing experience and allowing access to the d… A method of mitigating malware attacks is to ensure robust endpoint security.

It’s not mysterious or spooky; it’s home to everyday things like scientific research, medical records, private financial information, and secure communications. It also allows users to access the dark web, sites which cannot be viewed using conventional Internet browsers. The Tor Project recently launched a mobile version of its browser, allowing Android smartphone users to access the dark web.
Step 5: Start Browsing Hyphanet
These websites can be social media, news sites, weather forecasts, online banking, magazines and newspapers, cloud storage, and many others. Put simply, the deep web is all the information stored online that isn’t indexed by search engines. You don’t need special tools or a dark net browser to access most of the deep web; you just need to know where to look. Specialized search engines, directories, and wikis can help users locate the data they’re looking for. The dark web, which is what I’m discussing here, is a small subset of the deep web, and refers to websites that are specifically trying to stay out of sight.


