
Businesses should be aware of the potential for data leaks and invest in data loss prevention measures. Bitcoin is a particularly popular option, given its popularity in general, but other cryptos like Litecoin are also commonly used. This illicit use of cryptocurrency contributes to the popular misconception that it’s used mostly for illegal activity. There are a range of other kinds of data available on the dark web, including driving licenses, social media logins, and even home addresses. Payment card details are pretty commonplace on the dark web, with the price differing depending on the data provided. For example, if a CVV is not present, the price goes down, as this makes the card less useable.
Darknet Markets are online marketplaces where people can buy and sell illicit goods and services under the protection of the anonymity by TOR. The products that are most commonly listed for sale include drugs, fake documents, fraud-related items, and hacking services and tools. Cybersecurity for small businesses must include Dark Web monitoring to identify whether their stolen credentials are being sold online. Choosing the best cybersecurity solution for small businesses involves implementing real-time threat detection and strong encryption to prevent data breaches before they reach illicit markets. Darknet markets continue to be a significant concern for law enforcement and society due to their association with cybercrime. The combination of anonymity and the variety of illicit goods available make these platforms appealing to cybercriminals.
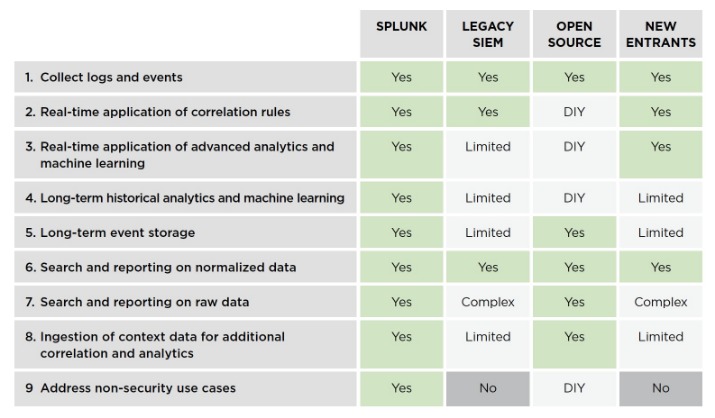
- Palo Alto Networks Next-Generation security platform provides a holistic solution to protect the digital way of life by safely enabling applications and preventing known and unknown threats across the network, cloud and endpoints.
- Bitcoin have been the most well-known cryptocurrency however new currencies are emerging such as Zerocash, which claims to be a privacy-preserving version of its predecessor.
- Recent trends show a surge in the sale of sophisticated malware, which can be used to infiltrate corporate systems or steal sensitive information from unsuspecting individuals.
- To do this, we extracted cyber-intelligence from darknet markets to provide a threat assessment of ransomware distribution.
Exploring The Hidden Web: A Guide To onion Links

Data, whether in the form of simple user credentials and passwords or proprietary trade secrets, can fetch quite a price on the dark web. The dark web might not interest you, but its denizens might have already cast their eyes on you, so approaching all of your business processes from a security-by-design perspective is essential. Singularity™ Threat Intelligence provides insights into adversary tactics and helps mitigate these risks before they impact your organization. Protecting endpoints with Singularity™ Endpoint Security ensures that these threats are detected and neutralized.
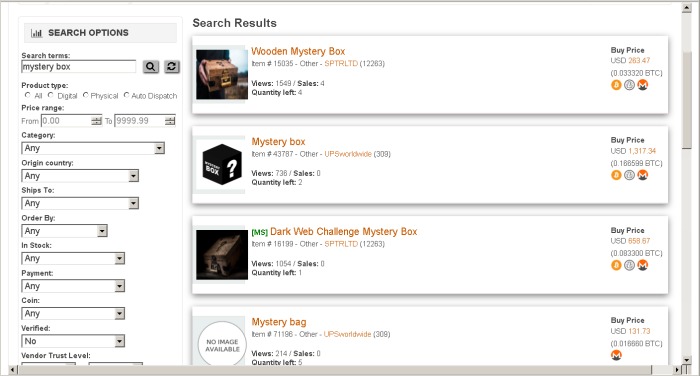
Selling Hacking Tools And Services
Between AI-driven algorithms for product verification and blockchain-based systems ensuring transaction integrity, emerging technologies are set to reshape dark web marketplaces profoundly. These developments could lead to improved trust among users while complicating the challenges faced by law enforcement. These addresses cannot be resolved by conventional DNS servers, contributing to the hidden nature of darknets. They can make purchases with your money with your payment details, use your streaming account for entertainment with your email address, or even receive free medical care using your social security number.
How To Access The Dark Web Safely And Anonymously
Legally, they are limited to observing publicly accessible areas using tools like the Tor browser, without engaging in unauthorized access or illegal transactions. The advent of the internet has brought about numerous conveniences and advancements in our daily lives. However, it has also opened doors to nefarious activities carried out by cybercriminals who exploit the digital realm for their malicious intents. Classic darknet markets sell diverse illegal goods; data stores focus on leaked or stolen data like credentials, databases, and ID records. The global cost of cybercrime has been on an alarming rise with the estimated loss to be in billions of dollars, with some reports indicating that the overall loss could be in trillions. A large portion of this cost can be attributed to the fraud conducted due to stolen PII data, some of which we have covered in this blog.
How Hackers Trade Data On The Dark Web
Internal pages from your Internet Banking site or other such internal post-login pages, dynamic pages, and such. They include Devian Behavior (six papers), the American Journal of Criminal Justice (five), the International Journal of Cyber Criminology and the Journal of Money Laundering Control (four per each). Surprisingly, the highest journal’s locally cited source (the International Journal of Drug Policy) was excluded from these three Zones (see reasons in “Implications” section). They use pseudonymous wallets, privacy coins (like Monero), mixers, chain-hopping, and non-KYC platforms to obscure transaction trails. In 2023, the dark web attracted an average of 2.7 million daily users, with Germany now leading as the country with the highest number of Tor users, surpassing the United States for the first time in years. Payments are typically made using cryptocurrencies like Bitcoin, which provide a layer of anonymity.
Is It Illegal To Access The Darknet?
Businesses face severe consequences when their data is leaked, from regulatory fines under data protection laws to reputational damage that erodes customer trust. Small businesses, in particular, are attractive targets due to often-limited cybersecurity resources, making preventing data breaches a priority for sustainable operations. Since some darknet markets were dismantled, vendors had also recognized authorities’ potential takedowns of marketplaces, which they counter by operating in multiple markets simultaneously. The variety of illicit goods and services’ marketplaces on the virtual platform have been prioritized to assess and publish by the different authors and co-authors. In conclusion, cybercriminals use darknet markets as platforms for a variety of illegal activities, exploiting features that provide anonymity and security.
One of the central76 discussion forums was Reddit’s /r/DarkNetMarkets/,777879 which has been the subject of legal investigation, as well as the Tor-based discussion forum, The Hub. MFA enhances security by requiring multiple authentication factors, reducing the risk of unauthorized access, even if credentials are compromised. It is considered an outright necessity by some in order to encourage free speech, maintain a free press and support the work of law enforcement and government agencies. OnionLand is also the name of a prominent site that acts as a major search repository for finding items on the dark web.
Distributing Malware And Ransomware
Transactions typically use cryptocurrencies for payment, with escrow systems protecting both buyers and sellers. They speak directly that they are aggressive, eager to fight with any adversaries that want to disturb their business and they are ready for global expansion in the darknet Market sector. Darren Guccione is the CEO and co-founder of Keeper Security, the world’s most popular password manager and secure digital vault.

In addition to that, the mobile malware enables criminals to intercept 2FA code sent via SMS by the bank or to redirect an incoming call containing verification details. They said also that this new darknet solves many known TOR problems and it has been successfully tested in China and Turkey. If the new Hydra darknet marketplace does indeed begin operations, it would become a significant part of the cybercriminal environment in the English language sphere. There is huge momentum behind the Hydra crew and the present moment is perfect to take over a large part of the illicit market on the darknets. It is also possible that these new projects won’t launch (or they will be operating only partially) and that Hydra’s Initial Coin Offering (ICO) was only a fraud targeting the darknet community. Lots of criminal activity happens on the Dark Web because it offers the anonymity that enables hackers and scammers to go undetected — but only up to a certain point.
You can also find secure email services, independent journalism platforms, and even the dark web Wiki. On the Silk Road, you could buy banned energy drinks, hacking services, digital goods (such as malware and pirated software), and forgeries (such as fake licenses and other illicit documents). But the most common and lucrative trade on the Silk Road was for drugs — by 2013, 70% of the products for sale on the Silk Road were drugs. You face significant risks when using dark markets, including scams where vendors take payment without delivering goods. There’s high exposure to malware and cybersecurity threats that can steal your personal information.
The cloak of secrecy provided here is what keeps these dark web marketplaces bustling with illegal activities, posing a significant challenge for cybersecurity experts and authorities worldwide. Darknets and dark markets have fueled the growth of cybercrime, provided a marketplace for cyber threats, and expanded the attack surface for malicious actors. When stolen data is exposed on Dark Web marketplaces, businesses face regulatory penalties, financial losses, and loss of customer trust.
If a company suffers a cyber breach, for instance, the place where the data is most likely to appear is on the dark web — either for sale or to be shared with other cyber criminals. AlphaBay then became the world’s dominant darknet market after its launch in December 2014. But it too was shut down by the FBI in July 2017, at the same time the Canadian citizen who ran the site from Thailand was arrested. Bitcoin transactions – Another aspect of anonymity in darknet markets is the use of Bitcoin transactions. Bitcoin transactions are conducted using public and private keys, which ensure that all transactions are secure and private. Bitcoin transactions are also irreversible, which means that once a transaction is completed, it cannot be reversed.
You can legally browse darknet sites for legitimate purposes like research or privacy protection. However, engaging in illegal activities on the darknet is against the law and can result in serious criminal charges. If you access illegal content or participate in criminal transactions, you face legal consequences. The legality depends on your activities and your country’s specific laws regarding darknet use. Dark markets often employ end-to-end encryption for communication between buyers and sellers, enhancing security and privacy. This encryption ensures that messages cannot be intercepted and read by third parties, including law enforcement.



