University of New South Wales in Australia, Concordia University in Canada, and Arizona State University in the United States have high research productivity and Influence. And yet, what Monero might be best known for in the general public is its now-common usage in illicit transactions. The currency is accepted on many large darknet markets alongside Bitcoin, and one of the largest dark web drug markets, the now-defunct White House Market, exclusively facilitated XMR transactions starting in late 2020. At KELA, we help you identify and mitigate risks by providing actionable intelligence from the darknet. Our solutions empower you to monitor illicit darknet marketplaces and track emerging threats, ensuring you can take proactive measures to protect your organization and reputation. Since its launch in 2021, Mars market has become one of the most secure and efficient darknet marketplaces.
A further limitation of bibliometric analyses that rely on abstract databases such as Scopus or Google Scholar is that the coverage of these databases may need to be completed. These databases may include only some relevant papers, particularly those published in less well-known or less prestigious journals or languages other than English 86. This can lead to a biased view of the research landscape, as papers not included in the database will not be included in the analysis. Several potential research areas are related to the Darkweb, phishing, and cybercrime. We used VOSviewer 46,47 to create a visualization of the keyword co-occurrence network.
‘Tokenization Is Going To Eat The Entire Financial System’ Says Robinhood CEO
Moreover, we also analyzed open sources of data on the Internet, i.e. historical data obtained accessing online forums, blogs, specialized webpages and public databases, that have been integrated with data reported in previous research papers. Digital infrastructure and their architecture fuels platforms, websites and other artifacts, that exists within them thanks to the layered and modular nature of such complex systems (Constantinides et al., 2018; Yoo, Henfridsson, & Lyytinen, 2010). Digital infrastructure, also called information infrastructure or cyberinfrastructure, is a term which encompasses a socio-technical interconnected structure of systems, people and organizations (Henfridsson & Bygstad, 2013).
As these platforms continue to evolve, it’s important for users to stay informed and understand how they work. With the rise of decentralized marketplaces on the darknet, I thought it would be helpful to dive into how they work and why they’re becoming increasingly popular. This post aims to provide a comprehensive overview of decentralized marketplaces, their benefits, and how they differ from traditional darknet markets.

Data Availability Statement
The anonymous and encrypted nature of the Darkweb allows drug traffickers to operate without fear of detection by law enforcement. Due to its privacy-focused technology and popularity, Monero has become a cryptocurrency of choice for darknet markets in recent years. For example, two of the most active markets, The Versus Project and ASAP, accept Monero. Both offer an array of illicit goods, including hard drugs, malware, stolen accounts and more. User reviews and vendor ratings play a critical role in maintaining trust within these markets.
Author & Researcher Services
- Cryptocurrencies, especially Bitcoin and Monero, are commonly used for ransom payments due to their pseudonymity and global reach.
- Our findings show that networks and bottom-up information flows trigger actions for infrastructure formation while in traditional mechanisms individuals recombine, adopt or add solutions (Henfridsson & Bygstad, 2013).
- As complex systems, digital infrastructures are exposed to major breakdowns determined by the propagation of local failures into large-scale disruptions (Hanseth & Ciborra, 2007).
- In the below graph, the currencies included are Bitcoin, Bitcoin Cash, Litecoin, and Tether.
- Online buyer behavior is shaped by the beliefs that a marketplace will institute and enforce rules and procedures to mitigate the risk of opportunistic behaviors (Pavlou & Gefen, 2004).
Criminals employ layering and structuring methods to conceal their illicit Bitcoin transactions, which are hard to track and regulate. By breaking large sums into smaller transfers and leveraging multiple exchanges, they evade regulatory scrutiny. These methods exploit gaps in compliance frameworks, complicating efforts to track and prevent financial crimes. Criminals now purchase ready-to-use malware kits, phishing templates, and ransomware programs. These tools come with user manuals and customer support, enabling even non-technical actors to conduct complex cyberattacks.
Future Trends To Watch:
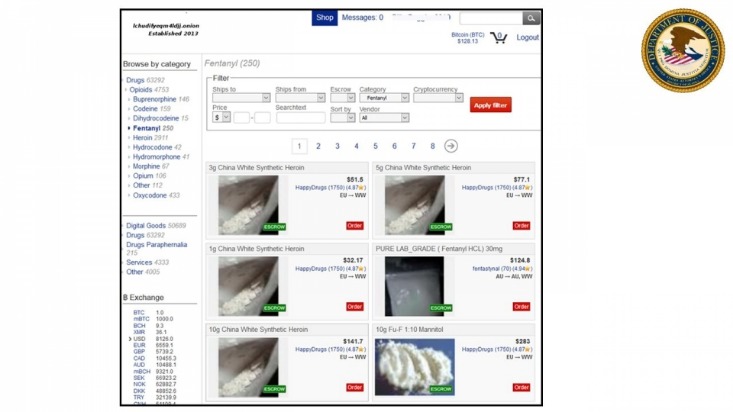
Card shops are a category of darknet market where users can purchase stolen credit card information. Similar to previous years, the vast majority of darknet market transactions flow through exchanges. Exchanges are by far the most common service customers use to send cryptocurrency to vendors, and for vendors to send funds to cash out. Now, places like ASAP are talking decentralized setups, spreading the load across nodes so they’re harder to shut down. I’ve seen some beta versions popping up on forums, and they’re rough but promising.
The pseudonymous nature and evolving tactics of criminals make regulatory oversight challenging. Strengthening Anti-Money Laundering (AML) and Know Your Customer (KYC) measures, along with advanced blockchain analytics and AI-driven monitoring, can help mitigate illicit activities while preserving the benefits of digital finance. Dark web operators use mainstream social media platforms to promote illicit goods. Advertisements for fake passports, stolen credit card dumps, and malware appear in private groups, often disguised with coded language. Once contact is made, vendors transition discussions to secure messaging apps to complete the transaction.
Effective And Efficient Projects For Creating A Cloud Environment Using Open Source Tools
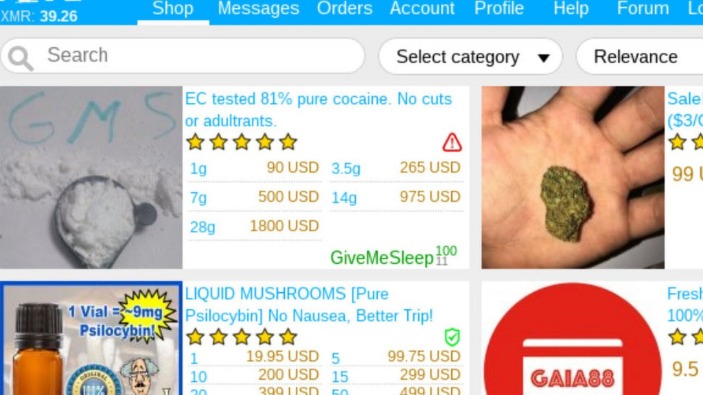
We draw on existing IS research to introduce the main features of OMs and review the primary factors influencing the performances of OMs. We then focus on social, technological and value-creating mechanisms explaining the functioning of OMs. Finally, we review the literature on OBMs to compare their mechanisms with OMs and evaluate how OBMs operate despite the adverse institutional conditions. One, casual drug buyers are shifting away from the darknet to make their purchases, while larger buyers are simply buying more per purchase. Current markets increasingly incorporate decentralization features, privacy-focused cryptocurrencies like Monero, and specialized focuses. Some have implemented distributed hosting, robust compartmentalization, and enhanced privacy features to mitigate centralized points of failure.
Monero And The Complicated World Of Privacy Coins
DEXs facilitate anonymous crypto-to-crypto swaps without identity verification, leveraging cross-chain bridges and privacy tools to obfuscate transactions. Some P2P enable off-ramping via cash and prepaid vouchers, bypassing AML compliance under claims of mere facilitation. Regulatory countermeasures, including blockchain analytics and the FATF’s Travel Rule, aim to trace illicit flows.
Several new marketplaces appeared, boasting improved encryption, decentralized infrastructure, and stronger vendor accountability. Many leaned into Monero (XMR) and other privacy-focused cryptocurrencies, abandoning Bitcoin due to its increasingly traceable nature. These platforms promised higher security, faster service, and tighter vetting of vendors—all in response to previous market collapses and law enforcement infiltration. Another key trend in the darknet market era is the growth of decentralized marketplaces. These marketplaces operate on blockchain technology, which provides a high level of security and anonymity. Decentralized marketplaces enable peer-to-peer transactions, cutting out the need for intermediaries, which can reduce the risk of scams and fraud.
US Senate Hearing On Crypto Taxes Reveals Headaches For Both Industry And IRS
“Monero takes privacy seriously. Monero needs to be able to protect users in a court of law and, in extreme cases, from the death penalty,” the site reads. We deliver contextualized, actionable intelligence through our dedicated platform or API integration, ensuring that you can respond effectively to darknet threats. This decline was triggered in part by the closure of prominent fraud shops like Bypass Shop, which was shut down in March. Brian Dumps, the biggest overall fraud shop for the year, also appears to have suffered a disruption as its revenue fell almost to zero in October, though it’s unclear exactly why. Dark Search is a relatively new free search engine tool that aims to make the dark web more accessible. This dark web search engine also has an easy-to-use interface and offers free access to onion links and websites.
Governments must adapt rapidly, crafting agile legal frameworks that balance innovation with accountability. Private cybersecurity firms must strengthen partnerships with regulators to track illegal transactions and monitor emerging threats. Blockchain analytics tools must evolve to include privacy coins and decentralized systems. Government-sponsored hacking groups actively exploit the dark web for intelligence operations, financial gain, and sabotage. These groups use dark web platforms to sell stolen secrets, acquire hacking tools, or coordinate with other criminal organizations. Cybersecurity teams must proactively monitor for leaked data and increase resilience against ransomware and phishing campaigns.
The main sources of these breakdowns are the occasional failure determined by admins, hackers and LEAs. One of the most significant developments in the darknet market era is the increasing adoption of cryptocurrencies. Bitcoin, in particular, has become the preferred currency for many darknet market transactions due to its anonymity and decentralization. However, with the rise of privacy-focused cryptocurrencies such as Monero and Zcash, the darknet market era is likely to see a shift towards greater use of these alternative currencies. As the internet has become increasingly integrated into our daily lives, it has given rise to a variety of new online spaces, including the darknet. The darknet is a hidden part of the internet that is not indexed by traditional search engines, and it is accessed using specialized software such as Tor.
Current State Of Darknet Markets
The result of this analysis was that although several mechanisms were at work, only the three mechanisms described in section 6 were consistent with all the data. One reason for the scarcity of research is the challenge of accessing the empirical field (Victor Benjamin, Valacich, & Chen, 2019). The success of OMs is also contingent on the level of participation and use of OMs’ functions. In addition to institution-based trust, online purchase intentions are influenced by the perceived social presence of a marketplace and the perceived social presence of others (Lu et al., 2016). For instance, when unanticipated market shocks reduce the number and types of traders utilizing OMs the lack of participation hinders OM performances (O’Reilly & Finnegan, 2010; Wang et al., 2008). But according to Ingo Fiedler, co-founder of Blockchain Research Lab, this trend is primarily the result of increasing law enforcement focus on the darknet market industry.
Tor2door Market
Machine learning and artificial intelligence techniques can analyze large amounts of social media data to identify patterns and trends related to the illicit drug trade and drug trafficking in the Darkweb. Data mining and classification algorithms can be applied to big data sets to identify suspicious activity and potential threats, making tracking and disrupting illegal drug networks in the Darkweb easier. Firstly, the study provides a comprehensive bibliometrics analysis of a corpus of 1068 publications from 2012 to 2022, including the pandemic period, which played a crucial role in the Darkweb’s use by both legitimate and illegitimate users. Secondly, this study identifies thematic areas of research based on science mapping analysis. Thirdly, while previous studies have examined related topics such as cryptocurrencies and Darkweb 14, 15, 16, our study is the first to examine the direct mapping of Darkweb research to SDGs. Lastly, the study identifies potential future research topics and provides a comprehensive overview highlighting under-explored areas that could inform future research.



