
Grant CREATE CONSTRAINT privilege to create constraints on all databases to the specified role. Grant CONSTRAINT MANAGEMENT privilege to create, drop, and list constraints for all database to the specified role. Update the properties for the database alias named database-alias. Create or replace a local alias named database-alias for the database named database-name. Create a local alias named database-alias for the database named database-name. If a database with that name exists, then the existing database is deleted and a new one created.
Because the Person node named Keanu Reeves already exists, this query does not create a new node.Instead, it adds a timestamp on the lastSeen property. Grant ALTER DATABASE privilege to alter standard databases the specified role. Grant SET USER HOME DATABASE privilege to alter the home database of users to the specified role. Grant CREATE INDEX privilege to create indexes on a specified database to the specified role.
Payment Methods And Escrow System
Cypher’s offerings are further enriched by unique custom hacking services, malware, and coveted data dumps, affirming its pioneering status in the darknet market space. Cypher distinguishes itself through its straightforward yet vibrant presentation. Beyond typical offerings like drugs and fraud-related goods, the marketplace is a repository of scarce and fascinating items, each detailed with compelling narratives.
Cypher Market – Small But Strong
By leveraging multi-layered encryption and secure protocols, even intercepted data is rendered indecipherable. Built for modern infrastructures, this solution integrates seamlessly into your organization’s IT framework, offering a robust shield against data breaches. With respect to Drupal, encryption/decryption of field values happens over ‘Cypher Link’ field-formatter. And currently, it has support for Links, Email, Text and Integer field types.
Discover The Best Cypher Url At Unbeatable Prices
The keys() function returns a LIST containing the STRING representations for all the property names of a NODE, RELATIONSHIP, or MAP. The sum() function returns the sum of a set of numeric values. The stDevP() function returns the standard deviation for the given value over a group.It uses a standard two-pass method, with N as the denominator, and should be used when calculating the standard deviation for an entire population.

Verified Market Links

The computer which was previously used for the password now has many different reactions based on what is typed in. Passwords will be recognized regardless of any spaces, emojis or punctuation inserted, except for question marks. On one out of every three touches of the computer knob there will be a backwards message. While 0xCipherLink provides strong encryption, it is essential to use a strong, unique password and ensure that the password is shared securely between sender and receiver. The security of the file transfer relies on the secrecy and complexity of the password used. The platform is in a phase of development, with its management team focused on rolling out significant improvements to enhance the user experience.
Secure Message Sharing
List the currently logged-in user, returns only the default outputs (user, roles, passwordChangeRequired, suspended, and home). Alter the default Cypher version of an existing standard or composite database.The available versions are CYPHER 25 and CYPHER 5. Create a point index with the name given by the parameter nameParam on relationships with the type STREET and property intersection.Point indexes only solve predicates involving POINT property values.
Torzon Market
Grant SHOW PRIVILEGE privilege to list privileges to the specified role. Grant SHOW ALIAS privilege to list aliases to the specified role. Grant CREATE ALIAS privilege to create aliases to the specified role. Deny SET PASSWORD privilege to alter a user password to the specified role. Grant ALTER USER privilege to alter users to the specified role. Grant SHOW ROLE privilege to list roles to the specified role.

The duration.inSeconds() function returns the DURATION value equal to the difference in seconds and nanoseconds between the two given instants. The duration.inMonths() function returns the DURATION value equal to the difference in whole months between the two given instants. The duration.inDays() function returns the DURATION value equal to the difference in whole days or weeks between the two given instants.

Add another way for the user to authenticate and authorize using the external provider externalProviderName.This provider needs to be defined in the configurations settings. If the specified user exists, force this user to change the password on the next login. This user will not be required to change this password on the next login. The user will not be required to change this password on the next login.
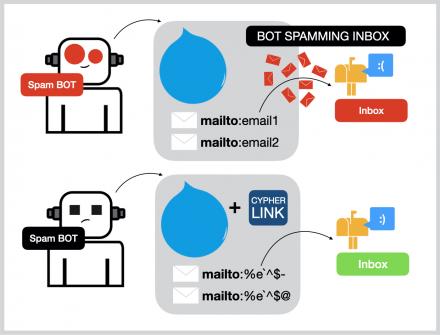
Here, concerned link items are encrypted at the server end (through PHP), and Javascript on the client side decrypts them to take appropriate action. Cypher Link module specifically targets BOTs’ email-spamming issue. BOTs read exposed ‘mailto’ Email IDs and spam individuals’ inboxes.At certain level, this module helps in overcoming email-spamming issue by exposing encrypted ‘mailto’ Email IDs to the BOTs.
Merge Single Node Specifying Both Label And Property
- List the currently logged-in user, returns only the default outputs (user, roles, passwordChangeRequired, suspended, and home).
- However, following suggested security practices reduces risk exposure to common threats and surveillance techniques significantly.
- The function startNode() function returns the start NODE of a RELATIONSHIP.
- In contrast to conventional markets, Cypher does not operate an account wallet system and instead processes all payments on a per-order basis.
- Map projection with a variable selector to project values based on a variable name.
The variety of encoding options keeps things fresh, and it’s really helped spark interest in cryptography among our members. Seamlessly switch between Caesar, Vigenère, and other popular encryption methods. Create varied levels of message security with different coding algorithms. Review the output to ensure it’s properly encoded or decoded.
The rtrim() function returns the given STRING with trailing trimCharacterString characters removed.If trimCharacterString is not specified then all trailing whitespace will be removed. The right() function returns a STRING containing the specified number of rightmost characters in the given STRING. The reverse() function returns a STRING in which the order of all characters in the given STRING have been reversed. The normalize() function returns a given STRING normalized using the NFC Unicode normalization form.



