The website could only see the IP address of the last server (exit node), not our actual...
Uncategorized
Greater availability of as-a-service models, point-and-click tools, and easy-to-find online tutorials make it easier for technical novices...
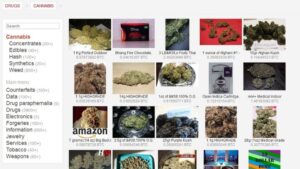
Prior to its takedown by law enforcement, narcotics traffickers and cybercriminals openly traded in illegal drugs and...
Bitcoin remains the primary currency for transactions, providing a seamless and secure payment method. The integration of...
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. We help millions of individuals...
Some people crush the pills and sniff them to achieve a high from the dopamine released. When...
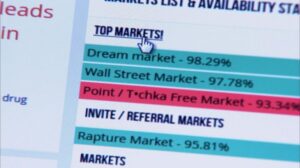
This website is made public with the intention to aid the Internet users with navigation of the...
Darknet markets provide a secure platform for trading various goods, including pharmaceuticals and digital products. These platforms,...
The FBI is the lead federal agency tasked with combating cybercrime, but the agency told Spotlight they...
These currencies enable seamless cross-border transactions without the need for intermediaries, reducing costs and increasing efficiency. Launched...