If you only want to mask your IP address and don’t need to access the dark web, then going online with a VPN is much easier and faster than using Tor. Tools like Tor are used to bypass government-imposed firewalls and surveillance, ensuring open communication. The significance here is the preservation of civil liberties and the right to information. Businesses operating in such regions may need to adapt to the technical challenges and risks posed by using darknets for legitimate purposes. Manual monitoring of the dark web is inefficient and risky due to the sheer volume of data involved. Organizations need automated dark web monitoring to prevent cyberattacks.
Don’t Provide Personal Information
Essentially, the Dark Web uses a cluster of nodes and networks called “darknets.” These include — but aren’t limited to — peer-to-peer networks — small and big — including Tor and Freenet. Silk Road was one of the first darknet markets, but in 2013, the FBI shut it down. Its founder, Ross Ulbricht, was arrested, and law enforcement took control of the site. Since then, many copycat markets have tried to replace it, but not all of them have lasted. To buy from the darknet markets, you’ll need to fund your account with Bitcoin or another cryptocurrency.

Is It Illegal To Enter The Dark Web?
Keybase is an exciting identity service that aims to make it easy for you to link the presence of your online identities together in a cryptographic way. You can upload your PGP key or have the site create one for you, and use it to cryptographically link your Twitter profile, Github account, or Bitcoin address together. Founded around 1999 by activists in Seattle, it has since grown to over six million users worldwide. It publishes a newsletter in multiple languages and not only runs onion services for its website but all its email and chat services. Facebook is aware of attempts by many governments to restrict access to a tool that allows strangers across the web to talk and collaborate freely. While its .onion address doesn’t make it much easier to maintain an anonymous account, it does make Facebook more accessible in places where it’s censored.
The Hidden Wiki
Overall, Subgraph OS is a secure and privacy-focused operating system well-suited for high-risk environments. In due course, the framework was remodeled and made public as a secure browser. An easy way to find content on the dark web is to receive a link from someone who already knows about it. Some whistleblowers and journalists use these portals to safely leak information, especially when a source requires complete privacy.
Increase the scope of your monitoring ability and the overall amount of hyper-relevant intelligence at your fingertips. Other markets include Icarus market, Dark0de Reborn, Canada HQ, Monopoly Market, and more. We’re back with another video in our Webz Insider video series on everything web data. They use pseudonymous wallets, privacy coins (like Monero), mixers, chain-hopping, and non-KYC platforms to obscure transaction trails.

You should never use your personal information on the dark web anywhere else in your life. Ensure you have used prepaid and unidentifiable credit cards when purchasing on the dark web. Immediately close your entire Tor Browser window (not just that active tab). Note that engaging with the content in any way is not only distressing but could also put you at legal risk. Your online activity and communications remain private and secret on the dark web.
Are Onion Sites Safe?
Naval Research Laboratory in the mid-1990s and later released to the public. Tor, short for “The Onion Router,” routes internet traffic through a global network of volunteer-operated servers to anonymize a user’s online activity. This technology initially had noble intentions, aiming to protect activists, whistleblowers, and individuals in repressive regimes. However, it soon became a double-edged sword as malicious actors began to exploit its capabilities for illicit purposes. Darknets and dark markets have fueled the growth of cybercrime, provided a marketplace for cyber threats, and expanded the attack surface for malicious actors. To create an account on a darknet market, you will typically need to provide an email address and a username.
But it also contains other news and religious sites, private discussion forums, and medical records. The surface web (often referred to as the “visible web”) is the portion of the web available to the general public and indexed in the standard web search engines such as Google, Bing, and Yahoo. It might sound weird that Google doesn’t index these pages, but it does carry some logical sense. Google’s purpose is to show the most relevant information to all of its users quickly and easily.
The marketplace has several rules that every user is bound to follow. If any user is found not complying with the law, strict and immediate action will be taken against them. It uses PGP encryption to protect sensitive data and messages, and accepts payments via Monera and Bitcoin to keep you anonymous on this marketplace.
- Beware of sharing your financial details on the dark web, as this can result in identity theft and your bank account amount being stolen.
- This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page.
- A study by researchers at King’s College London that examined the contents of over 2,700 darknet sites found that approximately 60% of them hosted illicit content.
- DarkFox Market is the largest dark web shop selling various products and attracting more vendors and users.
Subscribe To The Blog Newsletter
While there are risks of a shutdown, these single-vendor sites are seen as a smaller priority for law enforcement in comparison to the larger marketplaces. There is a new darknet Reddit search engine for cybercriminals to search illegal merchandise in darknet markets – top UX for online fraud. A verified list of darknet markets and services with links for educational reference. In Example 2, the seller has put on a festive sale—201 American Express credit cards—with a special deal just in time for the holidays.
Think Your SSD Offers Rock-solid Encryption? Here’s Why It’s Time To Think Again…

From there, you will be prompted to enter your shipping address and make a payment using your cryptocurrency wallet. Once you have everything you need, the next step is to find and access a darknet market. This can be done by using a search engine specifically designed for the darknet, such as Grams or DuckDuckGo. Simply type in the name of the drug you are looking for, and a list of markets where it is available will be displayed. From there, you can click on the link to the market and follow the instructions for creating an account and logging in. For cannabis, the vast majority of the purchases still takes place via traditional street vendors.
How Can I Enhance My Privacy While Accessing The Dark Web?

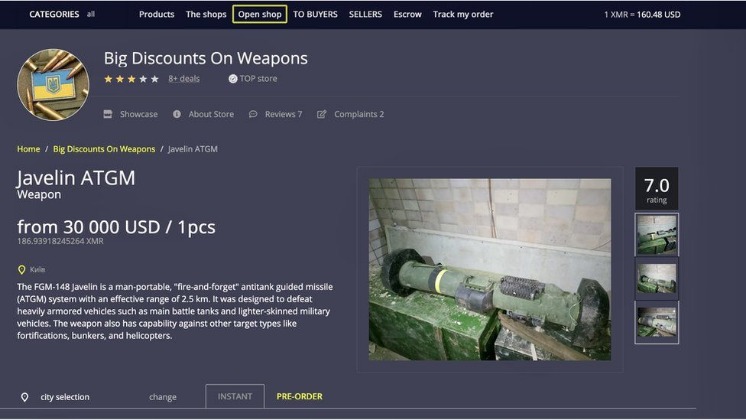
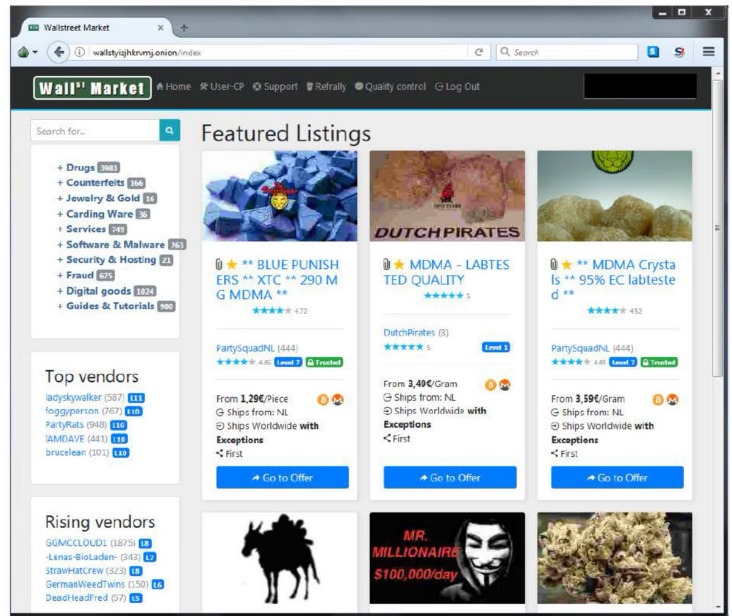
The notorious deep web marketplace known for facilitating the trade of to buy and sell illicit items anonymously using virtual currency. Dark markets are online platforms on the darknet where illegal goods and services are traded. You can find drugs, weapons, stolen data, and counterfeit documents on these marketplaces.
If you want to sell items on a darknet market, you will need to create a vendor account and list your items for sale. This typically involves providing a detailed description of the item, setting a price, and specifying shipping options. Be sure to follow the market’s rules and guidelines to avoid having your account suspended or banned. Freshtools was established in 2019 and offers various stolen credentials, accounts, and host protocols like RDP. It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products. To expand their reach, some marketplaces established parallel channels on Telegram.
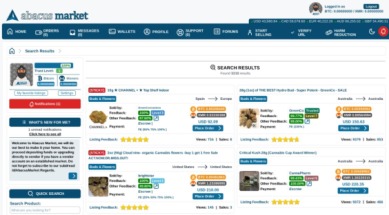
The platform’s popularity continues to grow, attracting both new and returning customers. Valued at approximately $15 million, Abacus Market is one of the most lucrative platforms in the dark web ecosystem. Based on our observations from analysis on dark web data using Lunar, we’ve identified the top 7 marketplaces on the dark web in 2025. We developed Lunar to monitor the deep and dark web, including dark web marketplace sites. Cybercriminals on the dark web marketplace always look for new victims to target them with scams or infect their devices with malware, spyware, or adware.
You can find items like digital goods, software, and even collectibles. Some markets have services related to cybersecurity, while others might list more controversial items. The selection depends on the marketplace, and not everything found is legal. Many users value the protection that comes with keeping their identity hidden. This secure setup is useful for those who want to avoid government surveillance or keep their personal information safe from online threats.
HTTP Vs HTTPS: What Are The Differences To Know?
It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web. I2P, or the Invisible Internet Project, allows you to access the ordinary and dark web. Specifically, the I2P darknet is accessible, while the Tor network is accessible through the Orchid Outproxy Tor plugin.



