
They serve similar goals but use distinct technologies with different benefits. Tor is completely legal in many places, including the U.S., EU, UK, and Australia, but illegal in others, like China and Russia. Due to illicit activities and dark web criminality, anonymous browsing is looked at with suspicion in certain countries. As with VPN legality, you should always check yourself and see if the dark web is legal in your country. As an extra weapon in your arsenal, install trusted antivirus software like AVG AntiVirus Free. With 24/7 protection, AVG can help protect your device from malware in real time, including blocking malicious websites and downloads that might be lurking on the web.
If the person tracking you is very advanced and has unlimited resources, they could conceivably de-anonymize you when you make certain mistakes, like downloading files or enabling scripts. Downloaded files could have malware in them that may be designed to de-anonymize you or infect your device. If you must download something from the dark web, only download files and run them using a completely isolated virtual machine. Though it still requires being routed through Tor (it is not a deep web browser by itself), it provides a clean, quick, and privacy-respecting base to use for your anonymous browsing sessions. Its main appeal is that it offers more privacy and supports legacy Firefox add-ons.

How Do I Find onion Websites Safely?
Tor works by routing your traffic through multiple encrypted servers, masking your location, and making it much harder to track your online activity. Because it’s the most secure option when it comes to anonymous browsing. It protects your identity, hides your location, and gives you access to .onion sites that are not available on the regular web. That’s why it’s the go-to choice for journalists, activists… and, of course, curious internet users.
Regulatory Measures And Legal Reforms
But remember, it’s essential to take all the necessary and important security steps before entering such sites on the dark web. As mentioned before, your ISP and government institutions are not able to see what sites you visit on the Tor network, but they can probably see that you use Tor. When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI.
This means your activities cannot be traced or your browser history exposed. Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc. Other sites explicitly block search engines from identifying them.
- Specifically, the I2P darknet is accessible, while the Tor network is accessible through the Orchid Outproxy Tor plugin.
- The second, less secure option is to use encrypted messaging apps with ties to specific non-profit or activist organizations.
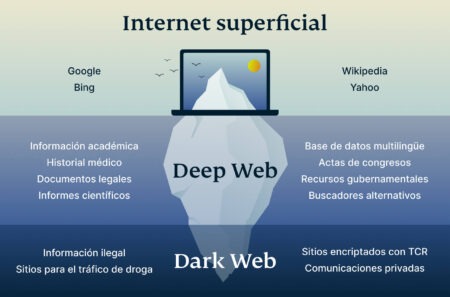
- The deep web is the next layer, and it encompasses a massive amount of online data that is not available for public consumption and not indexed by clear web search engines.
- AVG Secure VPN keeps you hidden no matter your network or browser.
This filtering distinguishes it from other dark web search engines that provide uncensored results. Ahmia can even be accessed through regular web browsers to find “.onion” addresses, although a dark web browser like Tor is still required to access them. The Internet we interact with daily represents only a fraction of the vast content available online. Beneath the surface lies the deep web, a realm of unindexed content, and within it, the dark web. The dark web is a segment of the deep web that is intentionally concealed and requires specific tools for access.
Risks And Dangers Of The Dark Web
If your device is unprotected, you could be a victim of malware or a hacking attack. We also recommend using a virtual private network (VPN) such as NordVPN — the best dark web VPN — to add an extra layer of protection. You can read our NordVPN review for more information, or try it out yourself using the 30-day money-back guarantee. However, though the dark web is synonymous with nefarious activity, it does have some benefits. We’ll also shed light on some of the legal uses of the dark web and show you how to access it securely in a detailed step-by-step guide. Endpoint Detection and Response (EDR) solutions are essential for defending against exploitation originating from the dark web.
Connect To The Tor Network

Tor is not itself illegal, but much of the activity on the dark web is illegal. Activities using Tor Browser are subject to the laws of each respective country. Depending on the country, even just accessing certain dark web sites may be illegal.
Users can easily open Tor-enabled private tabs alongside their regular browsing sessions, making it ideal for seamless and secure browsing experiences. DuckDuckGo offers an .onion version of its search engine, while Sci-Hub offers access to millions of scientific articles and papers. Library Genesis offers a search engine for collections of books on such topics as computers, business, technology, and more. These are only a few of the .onion search engines that are available. Because of the relaying of data through the onion nodes, and the encrypting and decrypting taking place at each node, your internet connection will slow considerably.
The 10 Best Dark Web Browsers In 2025
A key aspect of this configuration is the handling of JavaScript. Disabling JavaScript, especially on non-HTTPS sites (in “Safer” mode) or entirely (in “Safest” mode), is a widely recommended security practice when browsing the dark web. JavaScript can be exploited by malicious websites to track users, reveal their real IP address, or deliver malware. In such cases, the “Configure Connection” option becomes necessary. Clicking this button will lead to a series of configuration options designed to help users bypass censorship or accommodate specific network setups.
Tools Needed For Safe Access
You could consider the clear or surface web the “top” and visible layer of the internet, easily accessible using a browser such as Safari, Chrome, Edge, or Firefox. When considering anonymous browsing, Tor isn’t the only option available. VPNs, proxies, and alternative privacy-focused networks like I2P and Freenet also offer unique advantages. Understanding the strengths and limitations of each solution helps you select the best tool for your specific needs. The dark web can be dangerous due to the presence of scams, cybercriminals, and malware.
It works as a decentralized, peer-to-peer network that emphasizes censorship resistance and complete anonymity. The dark web is a hidden part of the web that is not indexed by traditional search engines like Google and requires specialized software to access. Lokinet is easier to set up than I2P, and it may run faster than Tor in some cases, especially when visiting regular websites through its secure network. However, its network is still small, and there aren’t many hidden services available yet. While accessing the dark web isn’t necessarily wrong or illegal, it’s important to know how to navigate this part of the internet safely.

It also keeps the graphical copy and text of the page for better accuracy. Using the ProtonMail .onion site offers security and privacy advantages. Moreover, the company also uses HTTPS and SSL encryption on the Onion site for extra protection. This makes it even harder for third parties to see your email traffic. It will offer you an additional layer of encryption to access the deep parts of the internet. The dark web is a part of the internet that you only step into with a specific tool (Tor, more on this later in the article).
- They are designed to index and retrieve information from hidden services that are not accessible through traditional search engines like Google or Bing.
- Functioning as a proxy, the Toorgle search engine crawls “.onion” links and presents text-based content and torrent files directly through its own interface.
- It allows users to create isolated profiles, each with its own digital fingerprint.
- To ensure one’s safety while exploring the dark web, it is crucial to steer clear of any illegal endeavors.
- Believe me – there are plenty to go around and each and every one of them are being kept under surveillance.
- Google considers the majority of the content on the entire web highly irrelevant and useless to its users.
Commercial Services
Everything you can find with a Google search is part of the surface web. In other words, every part of the web you can see and access by browsing normally. If you live in a regime that blocks Tor or need to access a web service that blocks Tor, you can also configure Tor Browser to use bridges. Unlike Tor’s entry and exit nodes, bridge IP addresses are not publicly listed, making it difficult for web services, or governments, to blacklist those IP addresses.
More On Tor Onions
Let’s find your key to safe access to the best dark web sites and anonymous browsing. This guide reviews tools such as Tor, I2P, Whonix, and more for accessing the hidden web securely. Dark web search engines exist, but even the best are challenged to keep up with the constantly shifting landscape. The experience is reminiscent of searching the web in the late 1990s.
His articles attract a massive audience of over a million users every month. He appears to be an expert with 10 years of experience in SEO and digital marketing. Damir has been mentioned in Mashable, Wired, Cointelegraph, The New Yorker, Inside.com, Entrepreneur, BeInCrypto, and other publications. He travels between the UAE, Turkey, Russia, and the CIS as a digital nomad. Damir earned a bachelor’s degree in physics, which he believes has given him the critical thinking skills needed to be successful in the ever-changing landscape of the internet. It’s a multiplatform problem-fixer that protects your entire digital life through a single app.



