
Proton VPN is part of the Proton family of services provided by Proton Technologies AG. While ProtonMail has a solid commitment to privacy, its location has caused problems for users in the past. In 2021, it was forced by the Swiss courts to begin logging the IP addresses and browser fingerprint information of one of its customers. Its inherent anonymity allows everyone from dissidents to whistle-blowers the opportunity to share information free from persecution.
Using a different browser than these could put your privacy at serious risk and could expose you to attacks from cybercriminals. As a general rule, it’s best to use the default settings in Tor or the Onion Browser. Changing any of the default settings can make websites misbehave or not load correctly. For the open web, just type your name into Google and see what comes up.
- Additionally, configure your security settings to provide maximum protection, such as firewall activation and using a VPN, while browsing the dark web.
- Unlike the Dark Web, the hidden corner of the internet often used to conduct illicit or anonymous activity, anyone can get to the Deep Web safely using a regular browser.
- And check your local laws to find out if accessing the dark web is legal.
- The Tor network anonymizes user traffic by routing it through multiple relays, making it nearly impossible to trace back to the original user.
- By the end, you will have a clearer understanding of this hidden corner of the internet and the potential risks it presents.
Use Alternative Dark Web Networks (I2P & Freenet)
The dark web is a hidden part of the web that is not indexed by traditional search engines like Google and requires specialized software to access. Law enforcement officials can exploit that weakness using “Tor-exit-node” monitoring techniques to expose users’ IP addresses and potentially trace activity back to the original users. If you’re on the dark web to engage in illegal activity and your traffic passes through a compromised exit node, your secrets can be exposed. The dark web is part of the deep web and is hosted on darknets and encrypted networks like Tor, Freenet and Riffle.
Our mission is to simplify navigation in the complex and evolving world of the darknet. Here, you’ll find links to various resources, including educational archives, private forums, anonymous services, and more. As the digital environment evolves, so do the tactics employed by cybercriminals, law enforcement agencies, and privacy advocates. Staying safe and anonymous often means continuously educating yourself, adapting your methods, and refining your tools. Ultimately, the Dark Web is neither purely nefarious nor inherently virtuous—it’s a dynamic environment shaped by the motivations and actions of its users.
Official Websites And Documentation
Understand what activities are legal and illegal in your country to ensure you do not inadvertently engage in illegal actions while exploring the Dark Web. Ensure that your device and software are up to date with the latest security patches. Use reputable antivirus or anti-malware software to protect against potential threats that may exist on the Dark Web. Regularly scan your system for any malicious software or vulnerabilities. Exercise caution when browsing the Dark Web, especially when accessing unfamiliar websites or interacting with unknown individuals.
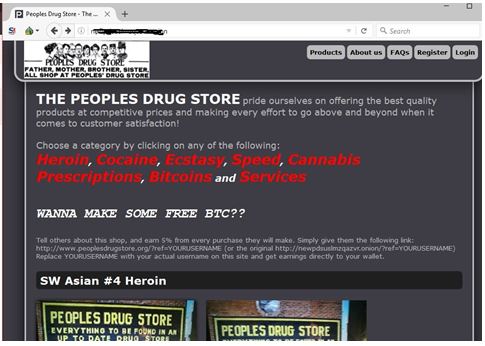
Drugs And Narcotics
This allows you to use public WiFi privately and without fear of hacking. There’s no chance of your real IP address leaking, while it benefits from some of the fastest speeds on the market. Using a VPN in conjunction with the Tor (The Onion Router) browser is the best way to access the dark web safely.
Cybersecurity Threats
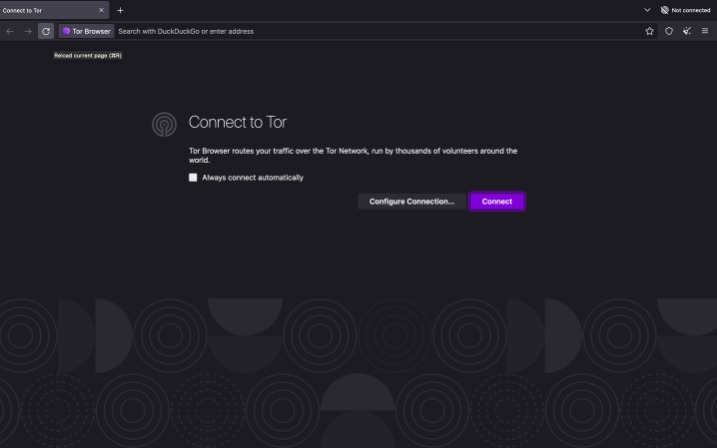
So, to get into the Tor network, follow the steps I’ve listed below. Especially for these people, the dark web is the perfect platform to communicate and publish information without having to worry about imprisonment or any other form of retribution. The purpose was to protect U.S. army soldiers and agents in the field, but also politicians who held secret meetings and conversations, which contained the highest security measures. The release of Freenet in 2000 is considered by many as the start or founding of the dark web. University of Edinburgh student Ian Clarke created Freenet as a thesis project.

Choose A VPN That’s Good For Accessing The Dark Web
Using a VPN alongside Tor adds an extra layer of security by hiding your IP address from Tor entry nodes and encrypting your traffic. This prevents anyone—including your ISP—from knowing that you’re using the Tor network. I2P, or the Invisible Internet Project, is an anonymous network layer to facilitate secure and private communication among its users. It works as a decentralized, peer-to-peer network that emphasizes censorship resistance and complete anonymity. DuckDuckGo is the best dark web search engine, as it offers an excellent user experience akin to surface web search engines. Its effectiveness in scouring the shadowy depths of the dark web can be likened to what Google does on the surface web.

For instance, you can create settings that disables JavaScript entirely to add an additional level of safety. For instance, there are some organizations who employ the services of white-hat-hackers for a number of reasons. To say the least, DOT Security does not recommend going to the dark web unless absolutely necessary. However, if you’re going to venture into the dark web, you’ll need to be well–prepared, so keep reading to keep safe. While you can visit the obscure part of the internet without a VPN, it’s better to go with one. Here are our favorite choices that work well and support Tor Over VPN perfectly.
These products are often bought with cryptocurrencies, and several markets thrive from this exchange to sell or buy products and services. Some popular marketplaces include AlphaBay (before it was taken down) and Hansa. Fraud and scams run rampant on the dark web, including offers too good to be true and fake services requiring upfront payment. Hackers sell access to email accounts, social media profiles, or other information that can be used for identity theft. If you use Tor to access the dark web or unblock websites, connect with a VPN for extra security.
- The dark web, being a hub for criminal activities like identity theft and malware distribution, exposes you to various security threats like malware or phishing.
- If your information has been compromised, then it’s likely that your phone number is also on the dark web.
- In case you’re wondering how to access the deep web, chances are you already use it daily.
- It encrypts your traffic right away, which is beneficial if you don’t want your ISP to see you’re using Tor.
- Although it’s not as widely used as Tor, I2P can provide robust anonymity and is well-suited for peer-to-peer file sharing.
How Do I Find onion Websites Safely?
You could easily use Tor in an attempt to pirate copyrighted content from the deep web, share illegal pornography, or engage in cyber terrorism. Using a legal browser will not make your actions fall to the right side of the law. The dark web, however, is a very concealed portion of the deep web that few will ever interact with or even see. In other words, the deep web covers everything under the surface that’s still accessible with the right software, including the dark web. The deep web rests below the surface and accounts for approximately 90% of all websites.
The dark web often connotes illicit activities like illegal drug sales and hacking. However, it also supports legitimate uses like protecting free speech and accessing information in censored regions. However, using the dark web for illegal activity can be a criminal offense.
Later, Tor’s underlying code was released under a free license, and a nonprofit called the Tor Project was formed. In 2008, the Tor Browser was released, which made it easy for anyone to get on the darknet. The existence of an anonymous and hidden internet then allowed for alternative information channels and illegal websites to flourish. Your information might be on the dark web if it was exposed in a data breach, sold, or stolen by hackers.
You should never use your personal information on the dark web anywhere else in your life. Ensure you have used prepaid and unidentifiable credit cards when purchasing on the dark web. It’s important to note that although the dark web has many valuable services, it is also a hangout for cybercriminals.
Again, it’s DOT Security’s advice to stay off the dark web entirely. The internet is almost unfathomably large, and most of us are only actively engaging with between 4-5% of it. If you manage to not expose your private information and avoid illicit activities, you can be sure everything will be okay. PIA is popular in the USA because it offers servers in all 51 states. People in the United States and abroad can use it to venture into the dark web in privacy.
If you stick to using it for legitimate and legal purposes and proceed with caution, you can have a perfectly safe and secure experience. This makes it almost impossible to track your dark web activity from beginning to end. Don’t get Tor confused with a VPN though, which uses tunnels to protect your data from lurkers. Learn the difference between using Tor and a VPN for anonymous browsing.



