Many sites on the dark web are scams, and some host illegal content. If you need to use a computer and do not want to leave evidence behind (like a digital ghost), Tails is the best tool. While it’s not a browser, it includes Tor Browser installed by default that provides anonymity for web browsing and enables users to access the dark web. This part of the internet is notorious for illegal activities, facilitated by the anonymity it offers. Crimes range from data theft and selling illegal goods for cryptocurrencies to human trafficking and more severe offenses. These search engines prioritize privacy and often index websites that aren’t listed on the surface web.
- This hides your Tor usage from local networks, masks direct Tor connections, protects against network-level surveillance, and reduces the risk of being flagged for accessing privacy tools.
- Using Tor is especially helpful in countries where authoritarian governments censor the internet, preventing citizens from accessing news outside their country.
- You can inadvertently download malicious software by visiting these websites, infecting your system.
- It offers outstanding privacy features and there is currently a discounted rate available through this link.
- It offers better speed and security than other alternative methods.
Hacking And Cybercrime Services
Open up Tor, and you won’t suddenly see the dark web staring back at you. Not only do you need a dark web browser, you need a dark web search engine too. This search engine will get you to the sites you need, though you can also go directly to dark web addresses if you know what they are, as with standard URLs. Cybersecurity has to also cover everything physically on your computer too—which law enforcement or government authorities might have the right to seize if they come calling. If you want to be untraceable and undetectable, connecting to the dark web via the Tor browser is a major step towards that, but not the only step you’ll need.
How Do I Access The Dark Web Safely Using Tor Browser?

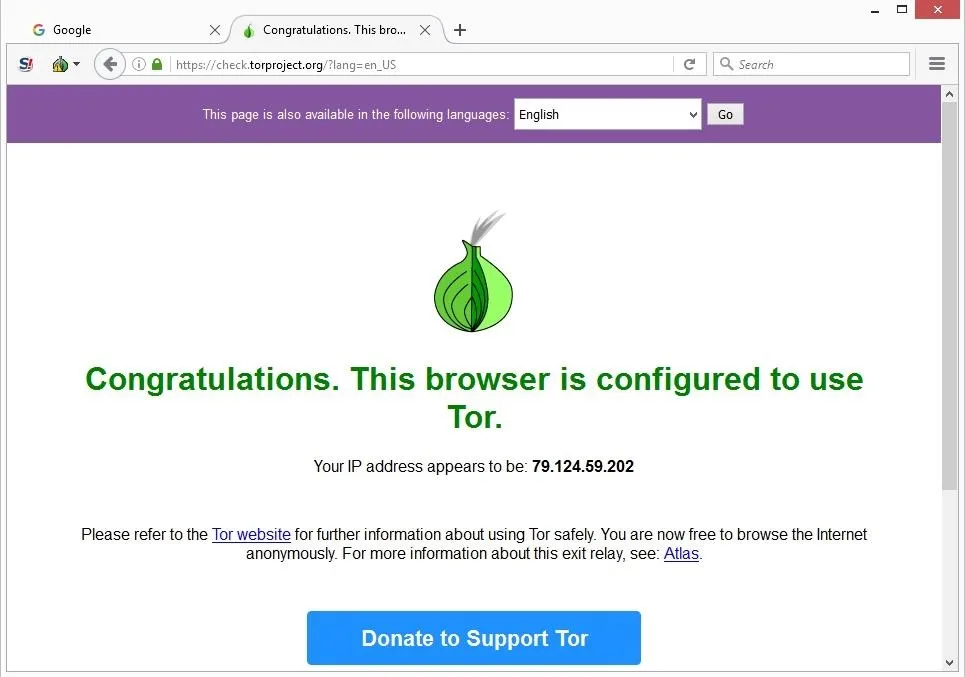
It is the closest thing to a full dark web online anonymity suite. The browser routes your traffic through a global network of volunteer-run servers (sometimes called nodes), encrypting your data and masking your IP address multiple times. To access the dark web, you must have specialized software, such as the Tor Browser. It creates a space for staying anonymous, which itself is kind of a double-edged sword. This guide reviews tools such as Tor, I2P, Whonix, and more for accessing the hidden web securely.
Using The Tor Browser
Its user-friendly interface and reliable protection are unmatched.” — Jamie L. You can download the Tor Browser for free from its official website at torproject.org. Be sure to only download it from the official site to avoid fake or malicious versions. I recommend using the Tor Browser with a good VPN for an extra layer of privacy and security. For most people, Tor over VPN is the safer and more practical choice.
Accessing Onion Sites On Android
These services are used to obfuscate the origins of cryptocurrency transactions, making it harder to trace them. Users can mix their digital currencies to break the connection between the sender and the receiver. While browsing online, you might have noticed that the websites you are visiting have URLs starting … Many countries, such as Qatar, China, Cuba, Russia, and Turkey, censor internet content promoting political dissent.
However, it is crucial to recognize the dual nature of the Dark Web, understanding that while it has legitimate uses, it also harbors risks and associations with unlawful activities. Users navigating this space should exercise caution and be aware of the potential legal consequences tied to specific content and transactions. Accessing the Dark Web requires the use of the Tor (The Onion Router) browser.
What Is The Dark Web? + 6 Tips To Access It Safely
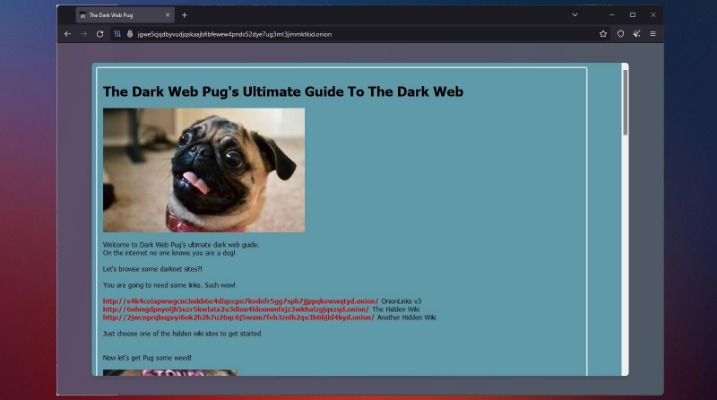
Companies use dark web monitoring to scan for leaked data, stolen credentials and breach indicators, helping them track and identify perpetrators. But let’s be realistic, the best defence isn’t just playing detective after the fact. It’s making sure your sensitive information never lands there in the first place. You have successfully accessed DuckDuckGo on the Tor Browser, enabling you to search the depths of the dark web while preserving your privacy and anonymity.

Swap Data In Countries That Censor The Internet
Not all dark web services are genuine, and many scam “.onion” sites offer downloads infected with backdoors and Trojan horses. Being cautious while browsing the dark web is essential, as significant risks are involved. Though not entirely shoddy, the dark web has a reputation for hosting illegal activities. It does support whistleblowers by offering them anonymity and secure communication in an oppressive regime. But navigating the dark web is full of cybersecurity and legal challenges.

This is one of the reasons why it is always good to hide your IP address. As much as the Darknet contains even the “good” stuff, it’s not a place you need to stumble about blindly without proper dark web safety. Cybercriminal groups like DDOS have carried out over 140 cyberattacks on companies since Bitcoin’s emergence in 2014. The attacks have led to the formation of other cybercriminal groups and Cyber Extortion.
The Darknet offers a place of free expression where not even a chunk of these limitations exists. Such sites include blogs, gaming sites, social media, and super-encrypted email platforms. Law enforcement agencies frequently target sites that distribute child pornography. For Example, In May 2021, authorities in Germany brought down Boystown, a child pornography network with more than 400,000 registered users. Several pedophile chat sites were also dismantled, and four people were detained, one of them a Paraguayan suspected of running the network.
Are There Alternatives To Tor Browser For Dark Web Access?
From in-depth reviews to the latest news and how-to guides, PCMag is the go-to source for staying ahead in the digital world. Although the dark web represents a small fraction of the totality of the deep web, it has attracted perpetual media attention over the last few years. You need a special browser to access it, and when you do, your internet traffic is not wired through the network of interrelated public servers in the way it is when you access the surface web. Engaging with these sites, even inadvertently, can expose individuals to serious legal consequences, including criminal charges.
Navigating Ransomware Attacks While Proactively Managing Cyber Risks
- While some threats on the dark web are well-known, others may use its notorious reputation to trick users into paying large sums of money.
- In 2018, someone gained access to a third-party data center in Finland.
- Second, it allows you to access websites or services that block Tor but accept VPN traffic, such as streaming or banking sites.
- Anything you need to do that has to be off the books to some extent, for noble or ignoble reasons, can be done on the dark web.
- The Dark Web has a social media platform called the Dark Web Social Network (DWSN), which is similar to regular social networking sites.
- Unlike Tor, I2P is designed for peer-to-peer services like file sharing, email, forums, and even decentralized websites — all within its own closed network.
Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down. When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI. The VPN is a second layer of extra protection, on top of the protection that the Tor network already offers. The users of the dark web are typically aiming to block governments from snooping on them. This can often be for political reasons, but also because they may be involved in illegal activities, such as the ones listed above. The dark web is a portion of the deep web that is intentionally hidden and requires specific software like Tor (The Onion Router) to access.



