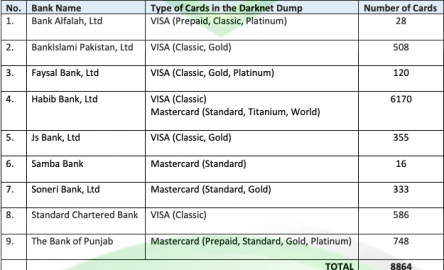
Additionally, monitor your credit report for any signs of new accounts or unauthorized activity. In conclusion, by following these best practices, you can significantly reduce your chances of falling victim to a credit card dump. While no method is foolproof, being informed and proactive in safeguarding your financial data goes a long way towards protecting yourself from cybercriminals. The breached data included names, addresses, phone numbers, Social Security numbers, credit scores, credit limits, and other details related to credit card applications. This data dump represented one of the largest breaches in history, with only the Equifax data breach (discussed below) eclipsing it in terms of scale. Credit card dumps have become an increasingly common concern in recent years due to their ability to impact a large number of consumers and companies alike.

B1ack’s Stash Reappears In The Media (February
This enables systems to detect fraud based on minute changes in transaction velocity, merchant category patterns, and even the time of day purchases are made. Rather than individual hackers working alone, the reality is that we’re dealing with sophisticated criminal enterprises that function like businesses, complete with customer service and quality guarantees. Join us as we break down and discover the methodologies of card fraud using our dark web monitoring tool, Lunar.
Torzon Market
“The most important thing is for people to keep an eye on their transactions and report any fraud immediately,” Krebs says. Unless you live the rest of your life only paying with cash, you’ll never be totally impervious to payment fraud. You may have never been to the dark web — but there’s a chance your credit card information has.
- Sellers often need to pay a deposit to prove they’re serious, and they build their reputation through positive reviews.
- Regularly updating software and implementing multi-factor authentication are essential steps that businesses can take to minimize the risk of credit card dumps.
- It’s been a constant back-and-forth between cybercriminals and law enforcement, with each new site trying to be smarter and more secure than the last.
- This data dump represented one of the largest breaches in history, with only the Equifax data breach (discussed below) eclipsing it in terms of scale.
The credit card dump industry presents a significant threat to the American financial industry, with Symantec estimating the value of stolen credit cards and bank accounts in the underground markets to be around $7 billion in 2008. A digital copy of the stolen credit card information is then created – referred to as a credit card dump. Credit card dumps are sold on the internet (including the dark web) to fraudsters, primarily through wire transfer or cryptocurrency. The fraudsters either use the credit card dump to clone credit cards to make unauthorized purchases at brick-and-mortar stores or online or to resell to other buyers. For companies handling sensitive customer data, investing in robust cybersecurity measures is crucial. Regularly updating software and implementing multi-factor authentication are essential steps that businesses can take to minimize the risk of credit card dumps.
Practical Tips To Prevent Carding Fraud
The incident was a wake-up call to both consumers and companies regarding the importance of data security and the potential consequences of failing to adequately protect sensitive information. Understanding the methods behind credit card dumps is essential for both individuals and businesses to take preventive measures against this type of cybercrime. In the next section, we will explore how consumers and companies can safeguard themselves from these attacks.

What Are Stolen Credit Cards Used For?

Blackpass is a dark web marketplace that has garnered attention for its clandestine offerings. At its core, this website provides a platform for the sale of stolen credit card information, making it a hub for cybercriminals. What adds to the intrigue is the anonymity of the operators, shrouding the website in secrecy. Despite the controversy surrounding its operations, Blackpass boasts a substantial user base and claims to have sold over 27 million dumps since its inception. To gain access to Blackpass’s offerings, users must pay a membership fee, adding another layer of intrigue to this dark corner of the internet.
Threat Actor Profiles
In 2023, the dark web attracted an average of 2.7 million daily users, with Germany now leading as the country with the highest number of Tor users, surpassing the United States for the first time in years. Your social security number can be bought on the Dark Web for less than you’d pay for a carton of eggs. Jake Taylor asked, “What’s on there?” Brandon Amacher, a cyber security expert and UVU professor said, “Everything. “Rescator, which has ties to Russian-speaking actors, started operating again in December 2021,” Intel 471 says. It’s unclear if Rescator is operated by the same proprietor as before, or if its infrastructure was sold to a new operator, the researchers say, but credentials tied to the old site were valid on the new shop, suggesting a link. Some fullz even include photos or scans of identification cards, such as a passport or driver’s license.
Censys’ Silas Cutler On How Adversaries Chain Vulns Together For Big Attacks
- Between January and August 2019 (when this database snapshot was apparently taken), BriansClub added roughly 7.6 million cards.
- A credit card dump refers to the unauthorized copying of credit card information from a user’s card.
- The largest known credit card dump to date occurred in 2017 when Equifax reported the theft of over 143 million records.
- The Federal Trade Commission oversees a website called IdentityTheft.gov, which provides the appropriate steps to report and recover from credit card fraud.
Further investigation indicated that B1ack started this marketing campaign in January this year by posting hundreds of free stolen payment cards to build credibility and attract more customers. There are entire websites, channels, and forums dedicated specifically to carding. Unlike other types of stolen data—such as email lists or personal information—carding exists as its own distinct niche within the cyber crime ecosystem.
Which Credit Report Does Chase Use
This time, the leaked data contains card numbers, expiration dates, and three-digit security codes (CVVs). The expiration for most cards reviewed by BleepingComputer ranges from 2025 to 2029, but we also spotted a few expired entries from 2023. It should be noted, however, that analysis of the previous data dumps showed that the data packs contained some duplicates as well as invalidated or expired cards, so a significant percentage of the free packs weren’t actually usable. All of these features, its competitive pricing, along with the volume of credit card information listings, make Real and Rare one of the prime sites to trade credit card information online. By way of example on hacking back, she pointed to the 2016 breach of vDOS — at the time the largest and most powerful service for knocking Web sites offline in large-scale cyberattacks.
Comey Indictment Centers Around Hillary Clinton’s Activities
As credit card dumps continue to pose a significant threat to consumers and businesses alike, it’s essential to stay informed about the latest trends and best practices in cybersecurity. By following the guidelines outlined above and maintaining vigilance against potential threats, you can help reduce your risk of falling victim to this type of crime. Remember that taking proactive steps today can save you from substantial financial losses, identity theft, and other consequences down the line. The black market for stolen credit cards is a massive illegal business, with cybercriminals getting their hands on card data in a number of ways. Point-of-sale card skimmers, targeted Magecart attacks on websites and info-stealing trojans are among their top tools for stealing credit-card data. The “massive collection of sensitive data containing over 1 million unique credit and debit cards,” was published to the criminal forum on Feb. 19 and contained six archives comprising a total of 1,018,014 cards.
STYX Market
This incident underscored the fact that even smaller companies could be vulnerable to large-scale cyberattacks, with potentially devastating consequences for their customers. Companies that suffer from data breaches caused by credit card dumps face various costs, including remediation expenses, notification fees, legal liabilities, and reputational damage. In some cases, these expenses can run into millions of dollars and may lead to significant losses in revenue or even bankruptcy. Organized criminal groups have recognized the potential profitability of credit card dumps and have turned it into a lucrative business model. These groups invest in advanced tools, techniques, and infrastructure to target victims and monetize their stolen data. They sell the information in various forms, such as individual card numbers, cardholder details, or entire databases, depending on the demand and price range.
Once the source is identified, the team can then assess the extent of the data loss and begin remediation efforts. Stick to cryptocurrency, avoid downloading anything, and don’t share any personal info. In 2019, there were approximately 8,400 active sites on the dark web, selling thousands of products and services daily. But the darkness of these deals doesn’t perfectly hide criminals from accountability.



