Accessing the Tor network through Tails OS (The Amnesic Incognito Live System) on a thumb drive is a highly secure way to browse the dark web anonymously. Tails is a portable operating system specifically designed for privacy, and it includes the Tor Browser by default. Here’s a step-by-step guide to setting up Tails on a USB thumb drive and using it to access Tor.
If you log into personal accounts on the dark web or visit websites with tracking scripts, then your activity may be tracked. Similarly, unless you’re using a VPN, your IP address will be visible to the first relay node you connect to. The dark web is also rife with scams, phishing attempts, and fraudulent services. Due to its largely unregulated nature, the probability of encountering scams is significantly greater than on the regular internet. Many websites are specifically designed to deceive users and steal their personal information, financial details, or cryptocurrency.
Best Onion Sites To Discover On The Dark Web In 2024

Setting up NordVPN will ensure that it encrypts your connection, so your ISP cannot see that you are using Tor. With the growing abilities of corporations to monitor and collect our data, the core principle upon which the dark web exists is now more relevant than ever. Brave is a browser based on Chromium that, by default, blocks ads and website tracking. This creates a faster and privacy-focused browsing experience without any configuration.
Step 2: Download Tor Browser

Again, not all the dark web is used for illicit purposes despite its ominous-sounding name. To help you make educated choices about cybersecurity to keep you (and your data) safe and secure, by providing detailed, accurate, and practical information based on thorough testing. When you’re done surfing or shopping on the dark web, don’t forget to shut down Tails. The major advantage of using a live OS such as Tails is that, on shut down, the OS wipes itself from the thumb drive you’ve installed it.
By following this dark web access guide, applying Tor browser safety practices, and knowing when it’s safe to browse the dark web, you can navigate responsibly without compromising your security. There are many different ways to access the dark web, but navigating it can be tricky and dangerous if you don’t know what you’re doing. A VPN will give you an extra layer of protection and anonymity, making it much safer to explore the dark web. Connecting to the Tor network might raise eyebrows depending on who and where you are.
How Does Tor Browser Work?
Your accidental visit to such sites can contribute to the perception of the demand, encouraging criminals to continue or expand their operations. Visiting the dark web, if you don’t exercise caution and have enough security, poses many security and legal risks that can lead to data theft, identity fraud, and legal consequences. Tor Browser prevents someone watching your connection from knowing what websites you visit. All anyone monitoring your browsing habits can see is that you’re using Tor.
- Keeping your VPN and Tor Browser updated ensures you benefit from the latest security patches.
- The editorial team did not participate in the creation of this guide.
- Make sure that when you download the Tor file, it’s from their official website.
- Originally developed to protect U.S. intelligence communications online, Tor is now used by the public for a wide range of purposes, both legal and illegal.
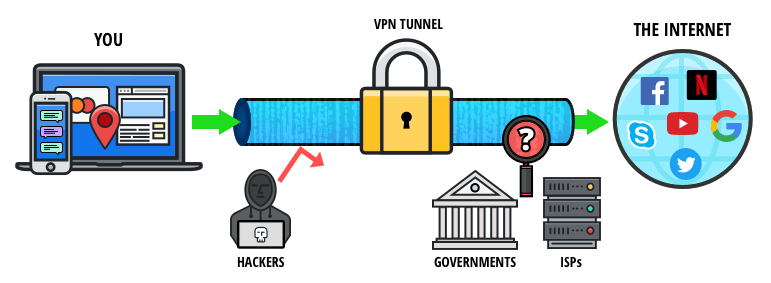
What’s more, it’s also hard to establish a VPN over Tor connection, as most VPN providers don’t support them. And even if you find a VPN that does, you’ll still need to perform a manual setup, which is inconvenient and time-consuming. That doesn’t mean it’s impossible to track users on the dark web.
Commercial Services

Of course, this sort of site poses no risk to legitimate dark web users, but it’s worth knowing that your usage of the dark web in general might draw attention to you. The following sections will explain how to access the dark web on different devices. However, remember to be cautious when accessing this hidden part of the internet. For added protection, it’s best to use a VPN like ExpressVPN to encrypt your internet traffic and mask your IP address while establishing the initial Tor connection. The term “dark web” refers to all of the content and websites of the internet that are effectively hidden from users, as they are not indexed by search engines and require special software to access. When accessing the dark web, consider using a virtual private network (VPN) to add an extra layer of security and anonymity to your internet connection.
Should You Use A VPN And Tor?
In rare cases, attackers can exploit an unsecure node to monitor Tor users or gain unauthorized access to accounts. Always verify a site’s legitimacy before visiting – onion addresses are long, random strings, making it easier for malicious actors to create lookalike addresses for phishing. A little typo can lead you to a clone designed to trick users into handing over sensitive data. Onion sites are hosted on the Tor network, enabling them to share information without revealing users’ IP addresses. They facilitate secure communication over the web and protect from third-party surveillance. Regular browsers can’t open Onion sites because they aren’t part of the standard domain name system.
How Do I Keep Myself Safe When On The Dark Web?
You will never know when you stumble upon illegal materials, inadvertently download malicious software, or expose yourself to identity theft. But if you must visit the dark web for ethical reasons, here are some safety precautions. Tor, short for The Onion Router, is a privacy-focused network that allows you to browse the Internet anonymously. It works by routing your encrypted traffic through multiple volunteer-operated servers, known as onion routers. Tor is by far the most widely used dark web network and is the biggest network in terms of content and activities.
Myth 1: The Dark Web Is Only Used For Illegal Activities
Hackers stole the data and threatened to upload it to the web if the site did not close down, and they eventually acted on that threat. The spouses of Ashley Madison users received blackmail letters demanding they pay $2500 in Bitcoin or have the infidelity exposed. You can also read our in-depth guide to using Tor if you want to know more about using the web anonymously and sending messages securely.
- PCMag has a guide for staying anonymous as you navigate the clear web.
- And once you’re inside, one wrong click on a fake .onion site can expose your identity or infect your device with malware.
- Once you are certain that you have the correct URL, save it in an encrypted note—the Tor browser will not cache it for later.
- That’s why dark web scans are important so you know if your personal information is compromised.
- To be on the safe side, we recommend combining the Tor or onion browser with a secure VPN, such as NordVPN.
- You can never be sure of the motive of the person operating the node that your traffic is routed through.
What Is The Role Of Relays In Tor?
In fact, a recent judgment by the US Supreme Court denoted that simply using Tor was sufficient probable cause for law enforcement to search and seize any computer around the world. Dark net websites are called “Tor hidden services“, and they can be distinguished from normal websites by their URLs. The terms “deep web” and “dark web” are sometimes used interchangeably, but they are not the same. Deep web refers to anything on the internet that is not indexed by and, therefore, accessible via a search engine like Google. Deep web content includes anything behind a paywall or requires sign-in credentials. It also includes any content that its owners have blocked web crawlers from indexing.
You need a special browser to access it, and when you do, your internet traffic is not wired through the network of interrelated public servers in the way it is when you access the surface web. For over 40 years, PCMag has been a trusted authority on technology, delivering independent, labs-based reviews of the latest products and services. With expert analysis and practical solutions across consumer electronics, software, security, and more, PCMag helps consumers make informed buying decisions and get the most from their tech. From in-depth reviews to the latest news and how-to guides, PCMag is the go-to source for staying ahead in the digital world.

The Tor Network provided a way to open safe communication channels for political dissidents, while also offering a channel for American intelligence operatives to communicate from around the globe. Journalists in overly restrictive countries also appreciate the anonymity of the dark web. That means that only 0.024% of all the known pages are findable in Google’s search engine. The users only have access to a fraction of the available data and web pages.



