If not prepaid cards, they may try the same thing with cryptocurrencies, or wire transfers. In this article, we delve into the dark side of credit cards and their entanglement with the sinister world of the Dark Web, shedding light on the dangers that lurk beneath the shimmering façade of convenience and ease. Prepare to be astounded, as we unveil the chilling reality that lies beyond the bright glow of your credit card statement. Thank you for joining us on this exploration of credit card transactions on the Dark Web. Stay vigilant, protect yourself and others, and make ethical decisions when navigating the vast landscape of the internet. The Dark Web, often mistakenly referred to as the Deep Web, is a clandestine part of the internet that is not indexed by traditional search engines like Google or Bing.

Taming AI’s Threat Vectors: Why CISOs Must Adopt A Secure Enterprise Browser (SEB)
The threat actor behind the AllWorld Cards marketplace has a clear goal in mind. They are actively promoting the platform on Dark Web hacking-related platforms since late May 2021. Telegram carding groups have become a significant threat in the cybercriminal community, with tens of thousands of members easily accessible through the chat application. Such type of data is likely to have been compromised online, making it a red flag for would-be fraudsters. Some vendors include access to a SOCKS5 internet proxy to help buyers avoid being blacklisted.
What Are The Risks Of Prepaid Cards?

Some threat actors offer a “complete package” known as “Fullz”, which includes full personal details and financial information like bank account details or social security numbers. Full or partial credit card details are commonly sold on the dark web, including BIN numbers, credit card numbers, expiration dates, and CVV numbers. One major online retailer saw a 300% increase in gift card theft after a major data breach. Customers who reused their passwords across sites found their accounts cleaned out overnight.
The State Of DDoS Defenses: Unpacking A New Survey Of 300 CISOs & Security Directors
“I always celebrate anybody who perhaps realises that they’re in an occupation, which is criminalised and decided not to enhance that further,” says Alex Hudson, the National Crime Agency’s head of darknet intelligence. For police, who would prefer criminals to face justice, this kind of exit causes mixed feelings. The darknet is a part of the internet only accessible through special browsing software. These dumps are sought for physical use, enabling activities like cash withdrawals from ATMs. Credit card prices also vary depending on the brand, with American Express being worth the most at 5.13 cents per dollar. A recent arrest in the Southeast Asia region marked the first time JS-sniffer operators have been caught anywhere in the world.

This proactive monitoring enables businesses to track and investigate potential threats in real-time, helping to prevent fraud before it can impact their operations. The use of such platforms is crucial for maintaining the integrity and security of customer data, and it provides an additional layer of defense against cybercriminal activities. Although there’s a variety of goods to be purchased on the dark web, one of the most sold resources by volume on the dark web, if not the most sold commodity, is stolen credit cards. Just last week, the largest carding site operator announced they would be retiring, after allegedly selling 358$ millions worth of stolen cards.
- Imagine entering a dimly lit room, filled with whispers and secrets, where the boundaries of legality blur into obscurity.
- By doing so, you can contribute to mitigating the impact of these illegal activities and help protect innocent individuals from falling victim to financial fraud.
- In addition to these types of listings, there are other free tools usually available on credit card sites.
- If gift cards are left accessible, he can simply grab the entire stack of cards, photograph the back of them, and later place them back in the tray.
- To avoid such losses, it is crucial to regularly monitor credit card transactions, report any unauthorized charges promptly, and take proactive steps to protect personal information.
Secure Your Personal Information
“The dumps also include magnetic stripe data, allowing criminals to create physical card clones,” Draghetti warned. In November of 2015, Will Caput worked for a security firm assigned to a penetration test of a major Mexican restaurant chain, scouring its websites for hackable vulnerabilities. So when 40-year-old Caput took a lunch break, he had beans and guacamole on his mind. He decided to drive to the local branch of the restaurant in Chico, California.
Design Community
The dark web has become a notorious hub for illegal activities, and credit card fraud is no exception. Criminals exploit the anonymity and encryption features of the dark web to buy and sell stolen credit card information. This underground marketplace offers a range of stolen credit card details, including card numbers, CVV codes, and even full personal information. Stay informed about the latest trends and tactics used by criminals to better safeguard your financial well-being.
Tracking Prepaid Card Data
It is important to note that engaging in such activities is illegal and unethical. The financial repercussions for victims can be debilitating, leading to damaged credit scores, fraudulent charges, and identity theft. Furthermore, participating in these illegal activities carries the constant risk of being caught by law enforcement agencies. Welcome to the dark underbelly of the internet, where secrecy reigns and illicit activities thrive. The Dark Web, a hidden part of the internet accessible only through specialized software, is a hub for illegal transactions, including the buying and selling of credit cards.

- Many other illegal darknet marketplaces have also shut down voluntarily over the winter for unknown reasons.
- Instead of limiting the number of requests, the company left their API open, allowing hackers to validate thousands of cards per hour.
- Each time a user clicks into an email thread, browses an unsecured website, or checks their account balance in a coffee shop, they could be exposing their data to potential fraudsters.
- Kaspersky advised that you should act promptly if you suspect your bank card details are leaked and monitor bank notifications, reissue the card and change your bank app or website password.
- This was followed by Monopoly Market, which became inaccessible early this month in what’s suspected to be an exit scam.
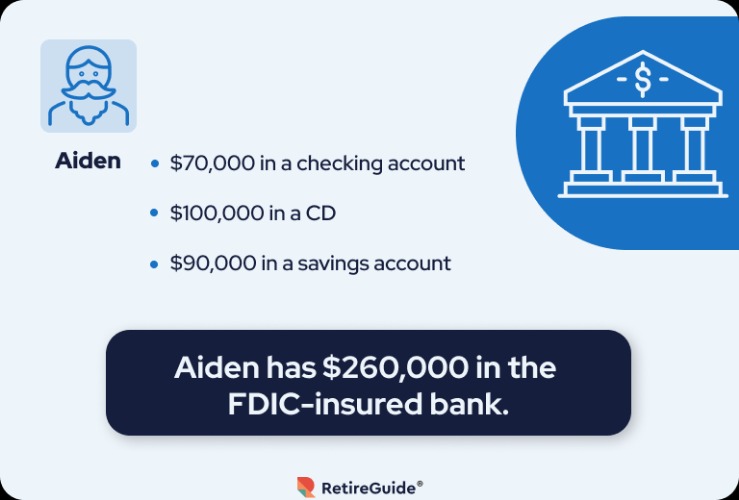
Some of most commonly-used include general purpose reloadable cards, prepaid debit cards, prepaid gift cards, and payroll cards. Unfortunately, fraudsters are also developing new tactics to siphon money out of this thriving market. The Federal Trade Commission reports that fraud involving gift cards made up $217 million out of the $10 billion lost to scams in 2023 alone. For individuals, that might be a utility company, telephone company, or HOA.
To pull off the trick, Caput says he has to obtain at least one of the target company’s gift cards. Unactivated cards often sit out for the taking at restaurants and retailers, or he can just buy one. From there, he runs the bruteforcing software Burp Intruder to cycle through all 10,000 possible values for the four random digits at the end of the card’s number, a process that takes about 10 minutes. By repeating the process and incrementing the other, predictable numbers, the site will confirm exactly which cards have how much value. “If you can find just one of their gift cards or vouchers, you can bruteforce the website,” he says. The initial bidding price was set for US$5,000 but the cards could be purchased outright for triple the amount.
However, this doesn’t prevent us from compiling the issuing bank of all those 50,309 cards. Historically when darknet sites close down, the operators disappear with customers’ or vendors’ money – this is known as an exit scam. It’s also the latest in a growing list of criminal marketplaces to have voluntarily retired in the last six months.
Some sellers even say that the cards can’t be tracked because of that same reason. Additionally, phishing scams and malware-infected websites are utilized to trick unsuspecting victims into providing their credit card details unknowingly. It is imperative for individuals to remain vigilant and exercise caution to protect their credit card information from falling into the wrong hands. It is understood that the data included such highly sensitive information as the primary account number of the credit cards concerned, along with expiration dates and the card verification value, CVV2, security code. But that’s not all; there are also cardholder details such as their full name, address, date of birth and telephone number as well as email address. Pretty much everything you would need to commit credit card fraud or launch phishing attacks against the cardholder.