The site’s dead simple to use, and vendors leave feedback that’s actually helpful. I’ve noticed they’re big on local vibes—vendors tweak their stock for where you’re at. Additionally, we analyse the U2U network of transactions, i.e., the transactions between pairs of market first-neighbors where the source and destination nodes are market users without the market as an intermediate. In the U2U network, an edge connects nodes that are not necessarily users of the same market.
Dark Web Markets: How They Work And Why They’re Dangerous
Dark web marketplaces may continue to evolve and present new challenges, but recent takedowns show that progress is being made. Among the array of tools available, advanced technology and international cooperation are key players in this ongoing battle. Along with the aforementioned factors, international cooperation is key to success in these operations. For example, the takedown of Monopoly Market was coordinated by Europol and involved authorities from nine different countries. The operation, codenamed SpecTor, led to the arrest of 288 vendors and highlighted the importance of shared intelligence and collaborative efforts across borders. See how our intelligent, autonomous cybersecurity platform harnesses the power of data and AI to protect your organization now and into the future.
Tweak Tor Browser Settings
The number of market-U2U and market-only buyers also drops as a consequence of operation Bayonet. However, compared to sellers, the drop is notably smaller, and the number of buyers rapidly recovers to previous values. Moreover, the number of multibuyers increases, which suggests a fast response from buyers to external shocks by trying to diversify their sources. With the advent of several markets at the beginning of 2014, the number of multisellers rapidly grows, representing more than 20% of all sellers until the beginning of 2016 (see Supplementary Information Section S3). During 2016 and 2017, AphaBay becomes the dominant market (see Fig. 3), polarizing sellers around its own ecosystem, such that the fraction of multisellers decreases to 10% of all sellers until its closure. Then, after operation Bayonet, the number of sellers in all categories and multisellers significantly drops, as shown in Fig.
Bonus: The Silk Road
But even if your online activity is private, security is still essential to avoid the threats that lurk online. Avast Free Antivirus is powerful threat-detection and anti-malware software that will help keep you safe online. One beneficiary of White House Market’s decision to close up shop might be the newly rebooted AlphaBay, now run by the admin “DeSnake.” DeSnake was one of the admins for the original AlphaBay but escaped prosecution.
Top 5 Deep Web Black Markets
As in the previous 3 years, we conducted research into the supply and prices of various goods and services sold by cybercriminals on the dark web. The RAMP forum is also considered “friendly” to Exploit and XSS, with one key differentiating factor. The forum widely accepts discussions about ransomware and seeks to welcome actors speaking languages other than English and Russian.
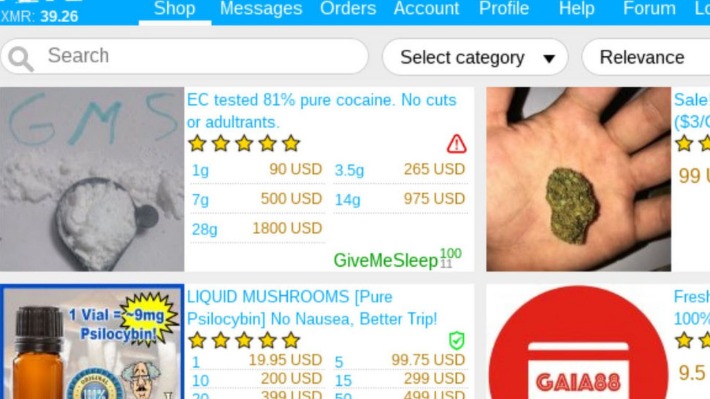
Real-World Examples: Data Breaches Feeding Dark Web Black Markets
Pros included a robust search system, responsive customer support, and a reputation-based vendor rating system. However, its rapid growth attracted law enforcement attention, and it was seized in 2017. The sudden disappearance of user funds during the takedown also highlighted the risks of centralized escrow systems.
First, while the dataset is preprocessed with state-of-the-art methods, there is no ground truth for validation, and this uncertainty propagates to our findings. For instance, we cannot verify if an entity classified as seller is in fact a seller. Similarly, there is no unique choice for the classification parameters or ground truth for fitting them. In light of this, we have chosen the parameters conservatively, obtaining estimates for the number of sellers that are in general smaller than the ones produced by other methods.
Collective Dynamics Of Dark Web Marketplaces

Data, whether in the form of simple user credentials and passwords or proprietary trade secrets, can fetch quite a price on the dark web. The dark web might not interest you, but its denizens might have already cast their eyes on you, so approaching all of your business processes from a security-by-design perspective is essential. In repressive regimes, darknets play a vital role in enabling free speech and access to uncensored information. Tools like Tor are used to bypass government-imposed firewalls and surveillance, ensuring open communication.

This structural change is reflected in the median net income of sellers and buyers, as shown in Fig. While the curves for the seller and buyer median net income were negatively correlated before Silk Road’s shutdown, after that moment they became positively correlated. Specifically, sellers show a trend of increase and buyers a trend of decrease in their median net income before the shutdown. Our classification shows that the number of sellers is significantly smaller than the number of buyers, as shown in Figs. The number of actors in the ecosystem is affected by several factors, especially market closures. Notably, the number of buyers and sellers significantly drops after the operation Bayonet in the last quarter of 2017, which shut down AlphaBay and Hansa markets, causing a major shock in the ecosystem34.
In a September interview with WIRED, DeSnake wrote that he reappeared to reestablish AlphaBay’s popularity as the go-to online black market. But weeks into the market’s relaunch, AlphaBay was still struggling to attract users. Undeterred, in his interview DeSnake said that dark web markets typically gain an influx of new users only after another popular market shuts down or is busted by law enforcement.

Transactions are conducted through Bitcoin and Monero which provides anonymity for both buyers and sellers. Bitcoin transactions are publicly recorded on the blockchain, which means they can be traced if you know what to look for. That’s why users often rely on mixers, privacy wallets, and other tools to make their transactions harder to follow. Beneath the visible layer of the surface web lies a hidden ecosystem known as the dark web. N 2025, dark web websites frequently change domains and are often short-lived. Accessing them may require .onion links and the Tor browser, but caution is advised due to legality and cybersecurity risks.
- Darknet markets trace their origins to the early 2000s, with the advent of Tor in 2002 by the U.S.
- Incognito’s all about keeping things easy and safe—perfect if you’re avoiding street buys.
- The site’s clean, escrow works like a charm, and the community’s buzzing about how reliable it is—definitely worth a look.
- Farwa is an experienced InfoSec writer and cybersecurity journalist skilled in writing articles related to cybersecurity, AI, DevOps, Big Data, Cloud security, VPNs, IAM, and Cloud Computing.
- If cryptocurrency is held in a customer account on a darknet platform, it’s always at risk if a site shuts down.
- However, its rapid growth attracted law enforcement attention, and it was seized in 2017.
We are pleased to present SuperMarket, the leading darknet market that aims to revolutionize the online shopping experience. While these guidelines may appear complex and bothersome initially, they will become second nature once you become accustomed to them. This is when you will develop a crucial sense of cybersecurity both online and in everyday life. Install anti-virus or other anti-malware software on your personal computer to scan for malware.
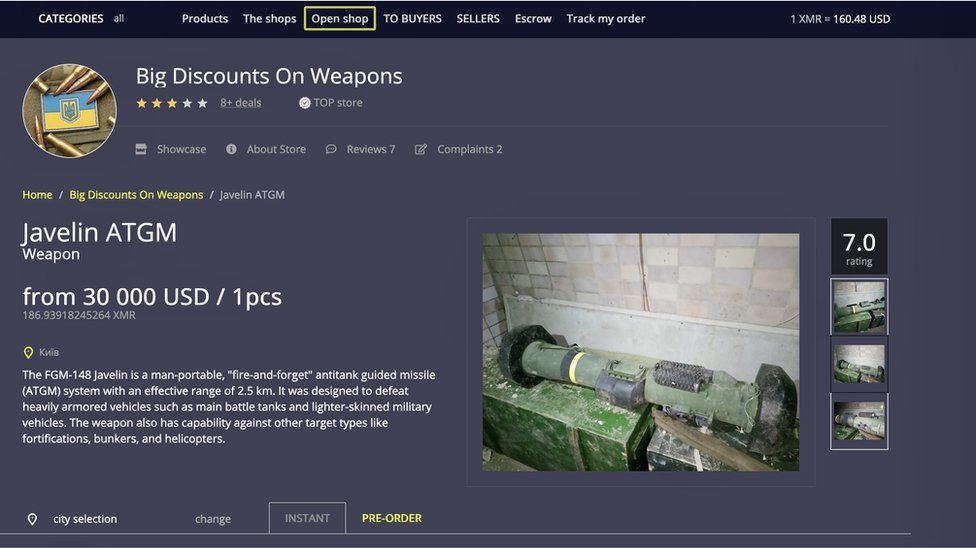
Analogously, we identify and characterise ‘multisellers’ (i.e., multihomers that are sellers) and ‘multibuyers’ (i.e., multihomers that are buyers). Furthermore, we analyse the seller-to-seller (S2S) network, i.e., the network composed only of transactions among sellers, which can be regarded as a supply chain network of illicit goods and services. We highlight that these networks exhibit different resilience regimes in the presence of external shocks, the ecosystem’s resilience being mostly guaranteed by the network of buyers rather than sellers. Dark web marketplaces aren’t just peddling the same old stolen credit card numbers and drugs anymore. These days, the types of illicit goods and services available have become far more advanced and dangerous. In fact, some of the most profitable illegal digital products on the dark web are crypto accounts, online banking credentials, and e-wallets.