Compromised credentials, stolen intellectual property, and leaked sensitive data regularly surface on dark web marketplaces, exposing SMEs to severe financial and operational consequences. Dark web marketplaces are structured platforms that mirror legitimate e-commerce websites but thrive on anonymity and untraceable transactions, often conducted through cryptocurrencies. According to a report by Kaspersky, a single stolen credit card can be purchased for as little as $15, while entire company databases are sold for significantly higher sums. These transactions present an ever-growing threat to businesses, particularly small and medium-sized enterprises (SMEs), which often lack the resources to counter these risks effectively.
Data Preprocessing
Edges are multihomers, i.e., traders that are simultaneously active in both markets (sellers in the multiseller network, and buyers in the multibuyer network). The width of the edges is proportional to the number of multihomers acting between the markets. With the advent of several markets at the beginning of 2014, the number of multisellers rapidly grows, representing more than 20% of all sellers until the beginning of 2016 (see Supplementary Information Section S3). During 2016 and 2017, AphaBay becomes the dominant market (see Fig. 3), polarizing sellers around its own ecosystem, such that the fraction of multisellers decreases to 10% of all sellers until its closure.
About SecurityWeek
For instance, we cannot verify if an entity classified as seller is in fact a seller. Similarly, there is no unique choice for the classification parameters or ground truth for fitting them. In light of this, we have chosen the parameters conservatively, obtaining estimates for the number of sellers that are in general smaller than the ones produced by other methods. Second, our approach does not explicitly classify buyers, which are entities that were not classified as sellers.
Set Up Tor Browser
Market takedowns create temporary disruptions, but they rarely dismantle entire networks. Sophisticated players shift operations, adopt new aliases, and resume business within weeks. Our technology scans the dark web for any mention of your sensitive data and sends timely alerts to protect your business from exposure.
Impact On Businesses And Cybersecurity
By ensuring compliance with cybersecurity regulations and prioritizing data protection, businesses can contribute to a safer digital ecosystem while avoiding the severe consequences of dark web-related risks. On top of that, undercover operations are a key strategy that’s being used, with agents posing as buyers or sellers to infiltrate these markets. The field of digital forensics also plays an important role since it helps investigations trace digital footprints back to their sources.
How Do Dark Web Markets Work?

Background research tasks included learning from past drug lords, researching legal matters, studying law enforcement agency tactics and obtaining legal representation. Patterns recommended to avoid include hiring hitmen like Dread Pirate Roberts, and sharing handles for software questions on sites like Stack Exchange. One of the central76 discussion forums was Reddit’s /r/DarkNetMarkets/,777879 which has been the subject of legal investigation, as well as the Tor-based discussion forum, The Hub. N 2025, dark web websites frequently change domains and are often short-lived. Accessing them may require .onion links and the Tor browser, but caution is advised due to legality and cybersecurity risks.
What Is The Dark Web? How To Access It And What You’ll Find
Cybersecurity professionals actively monitor these underground forums to identify leaked corporate information, using automated web crawlers, threat intelligence platforms, and Dark Web monitoring services. This approach enables businesses to conduct cybersecurity risk assessments and mitigate potential threats before they escalate into financial losses or compliance violations. The goods on sale range from stolen credit card data and forged documents to illegal drugs, weapons, malware as a service, and hacking tools. Dark web marketplaces are online platforms operating within the dark web, where individuals trade illicit goods and services while preserving their anonymity. Unlike traditional e-commerce websites, these marketplaces rely on encrypted networks like Tor (The Onion Router) and cryptocurrencies such as Bitcoin to conceal user identities and transactions. This unique infrastructure fosters an environment for illegal commerce, posing significant cybersecurity risks for businesses.
The Fall Of Silk Road And The Rise Of New Marketplaces
BidenCash administrators charged a fee for every transaction conducted on the website. The largest component of the S2S network of U2U transactions between sellers for each year with the respective number of nodes (N). The nodes are sellers that are active in that year, and an edge is placed between two sellers if at least one transaction occurs between them during that year. The network is mostly populated by U2U-only sellers, followed by market-only sellers.
Let’s get this straight — not everything on the dark web is illegal or harmful. In fact, some parts of it actually provide a safe space for privacy and freedom, especially where traditional internet access is limited or censored. The dark web hosts a variety of illegal activities, many of which fuel cybercrime and real-world harm. Darren Guccione is the CEO and co-founder of Keeper Security, the world’s most popular password manager and secure digital vault.
A VPN encrypts the data traffic and keeps your activities private on the dark web. It also masks your IP address, making it difficult for government agencies to monitor or track your activities. We recommend using NordVPN as it offers top-notch security features, including dark web threat protection.
Its intuitive interface and advanced search features make it easy to find local and global products. The marketplace extensively vets vendors listed within its deep web environment that offer a wide range of product portfolios, including security solutions, digital services, and specialized equipment. It stands as a reliable alternative to the defunct Alphabay Market as it continues to position itself as the premier source for advanced privacy-focused digital commerce. As cyber threats originating from the Dark Web continue to evolve, businesses—especially small and medium-sized enterprises (SMBs)—must implement proactive security measures to safeguard their sensitive data. A multi-layered cybersecurity strategy incorporating Dark Web monitoring, cybersecurity risk assessments, and employee training can significantly reduce vulnerabilities. This marketplace specializes in a variety of illegal products, including drugs, counterfeit documents, and hacking tools.
Buyers browse listings, place orders, and pay with cryptocurrency — typically Bitcoin or Monero — to obscure transaction trails. Law enforcement agencies keep an ear to the ground on the dark web looking for stolen data from recent security breaches that might lead to a trail to the perpetrators. Many mainstream media organizations monitor whistleblower sites looking for news. In spite of Huione Guarantee’s apparent too-big-to-fail strategy, the Elliptic researchers say that the platform is far from being totally self-sufficient. So far, Huione’s stablecoin and cryptocurrency exchange have failed to register significant volumes of transactions, Robinson says, despite some promotion within its existing communications channels. As the marketplace works to push the transition, its ongoing reliance on third parties could still be a weakness—at least for now.
These markets create parallel economies where criminal actors can trade freely without oversight from regulatory bodies. Advanced encryption technologies support anonymity, while cryptocurrencies ensure that financial trails remain difficult to follow. Much like familiar e-commerce platforms, dark web marketplaces are organized to offer a smooth buying and selling experience. However, they aren’t visible on the open internet and require specialized browsers like Tor to access. This added layer of encryption masks users’ locations, making it nearly impossible to trace activity back to individuals. Law enforcement agencies and international coalitions play a critical role in countering dark web activities.

However, the trend is clear—illicit actors are expanding their strategies, forcing enforcement agencies to evolve their tracking methods to keep pace with increasingly sophisticated laundering techniques. Most e-commerce providers offer some kind of escrow service that keeps customer funds on hold until the product has been delivered. Every communication is encrypted, so even the simplest transaction requires a PGP key. Medical records, fee-based content, membership websites, and confidential corporate web pages are just a few examples of what makes up the deep web. Estimates place the size of the deep web at between 96% and 99% of the internet.
- Governments must adapt rapidly, crafting agile legal frameworks that balance innovation with accountability.
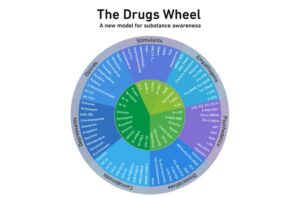
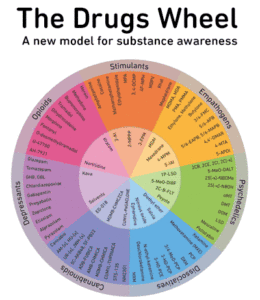
- They operate similarly to regular e-commerce sites but use cryptocurrencies for transactions.
- The use of digital signatures can also help verify the authenticity of users and transactions.
- Darknet marketplaces may look like regular online stores, but using or even browsing them comes with serious risks.

Alphabay Market leads with 60,000+ listings and $20 million in monthly trades via BTC and XMR, dominating 20% of darknet marketplaces. With 25,000+ users and 3,000+ vendors, it’s the gold standard for escrow security and scale. The scam ecosystem has been booming around the world, with criminals honing a handful of strategies to trick victims into voluntarily sending their money into the abyss. And as the cash—or, typically, cryptocurrency—flows in, a set of digital services and infrastructure offerings have increasingly emerged. The scam economy helps criminals with everything from creating fake social media pages to buying SIM cards—and, crucially, with money laundering. Now, researchers say that in the pantheon of dark web marketplaces, the “largest illicit online marketplace” ever is now one that sells services to other scammers rather than focusing on drugs or other contraband.
Although some of these markets prohibit certain extreme content such as violence or exploitation, most operate with very few rules beyond ensuring the security and anonymity of their users. Businesses must prioritize cybersecurity by implementing Dark Web scanning tools, strengthening access controls, and educating employees about emerging threats. Identifying security vulnerabilities before cybercriminals exploit them is essential for maintaining operational integrity. By implementing strong cybersecurity measures, SMBs can comply with cybersecurity regulations and safeguard their operations from Dark Web-related threats.