
These listings often include detailed descriptions, user reviews, and even shipping guarantees. Law enforcement agencies monitor many dangerous markets, and even anonymous browsing isn’t foolproof. Just visiting these sites can attract attention from law enforcement, especially if you interact with known vendors or download suspicious content. Dark web markets work much like regular e-commerce websites but with extra layers of anonymity and encryption. Buyers browse listings, place orders, and pay with cryptocurrency — typically Bitcoin or Monero — to obscure transaction trails. In this article, we’ll explore what dark web markets are, how they work, and why they’re so risky.
See how our intelligent, autonomous cybersecurity platform harnesses the power of data and AI to protect your organization now and into the future. In repressive regimes, darknets play a vital role in enabling free speech and access to uncensored information. Tools like Tor are used to bypass government-imposed firewalls and surveillance, ensuring open communication. The significance here is the preservation of civil liberties and the right to information. Businesses operating in such regions may need to adapt to the technical challenges and risks posed by using darknets for legitimate purposes. While Tor anonymizes your connection, a VPN adds an extra layer of security by hiding Tor usage from your internet provider and reducing traceability.
- Russian Market has consistently remained one of the most popular and valuable data stores on the dark web.
- Due to its extensive inventory and reputation for reliability, Brian’s Club has maintained a significant presence on the dark web.
- By encrypting user traffic and by bouncing it around the relay network at darknet market list random, Tor obfuscates a user’s activity.
- Once the buyer confirms satisfaction, the funds are released to the seller.
Bonus: The Silk Road
Although the Dark Web may seem intimidating and difficult to access, there are many tools available to help investigators uncover its secrets. With the right resources and investigative techniques, it is possible to identify those who are engaging in insider trading activities. For starters, dark web traders can use their access to financial data to identify and capitalize on potential discrepancies between the current market price and the future price of a given asset. Through the use of software programs and custom algorithms, traders can analyze patterns and determine whether or not there is an opportunity for profit. Additionally, by understanding how certain companies’ stocks move, traders can use their insights to trade in a more informed manner.
Frequently Asked Questions (FAQs) About Dark Web Marketplaces
One darknet user confirmed DeSnake’s key and that they were part of the original AlphaBay tech staff. As the cryptocurrency space continues to grow, more exchanges have emerged which provide competitive trading fees, exchange rates, and user-friendly features as they vie for more users and trading volume. Redditor claims to have been arrested & charged over SR1 cocaine sometime in 2012, but not convicted. Pistols were the most common item for sale, followed by rifles and sub-machine guns, the report reads. Panda, with the support of WatchGuard, has created a tool that use to scan the Dark Web and happens to check if the information.
EPF Nominee Update Online – How It Works?
In one particularly devastating case, a man lost his entire $80,000 pension. Using his credentials, cybercriminals committed a variety of online fraud activity over the course of six months. Another darknet market known for facilitating fentanyl sales to the United States was Canada-based AlphaBay.
Decentralized technologies now underpin a new generation of dark web markets. These platforms run on peer-to-peer protocols without central servers or administrators. Smart contracts manage vendor-buyer interactions, and blockchain-based dispute systems replace traditional moderators.
The Chainalysis 2024 Crypto Crime Report
One of the most common is the exit scam, where a marketplace suddenly disappears and takes everyone’s money with it. All of that means Telegram’s takedowns are by no means the end of the crypto-scam industry, says Robinson. They may, however, represent a serious setback for the markets that cash out its profits and launder its money. Whether the two markets succeed in relaunching, Robinson notes, will depend largely on how serious Telegram is about its efforts to prevent them from using its messaging services. Despite these efforts, dark web operators rebuild quickly, often with better security and decentralized tools.
Kraken Market also captured the largest share of transfers potentially sent for the purpose of obfuscating funds, as well as buying illegal products. In addition to that activity, markets like these host vendors that advertise their own cashout or swapping services, resulting in tens of millions of dollars in laundered funds. In Grand Theft Auto Online, players who purchase warehouses and garages for illicit cargo and stolen cars can buy/steal and sell them through trade on the “SecuroServ” syndicate website.
Two-Thirds Of Organizations Have Unfilled Cybersecurity Positions
For comparison, most midsize companies operating in the US earn between $10 million and $1 billion annually. Both Agartha and Cartel earned enough revenue within the 35-week period we tracked them to be characterized as midsize companies, earning $91.6 million and $32.3 million, respectively. Other markets like Aurora, DeepMart, and WhiteHouse were also on track to reach the revenue of a midsize company if given a full year to earn. The MITRE ATT&CK framework provides a comprehensive view of adversary tactics. Singularity™ Threat Intelligence provides insights into adversary tactics and helps mitigate these risks before they impact your organization. On average, deep Web sites receive about half again as much monthly traffic as surface sites (123,000 pageviews per month vs.
Fraud And Hacking Services

As these platforms grow more secure, decentralized, and integrated into broader digital ecosystems, their influence expands. Operators of these markets implement strict entry barriers, requiring encryption keys and multi-factor authentication. This focus on security ensures the anonymity of both vendors and buyers while making law enforcement infiltration more difficult.
Today, no single player is dominant like these marketplaces were before their takedown, with administrators preferring to specialize in particular types of goods and services. Apart from the dark web markets that are operating online today, some raided platforms influenced many markets. Active for a decade since 2014, it is a widely used credit card shop used to source stolen credit card information such as dumps, CVVs, Wholesale Accounts. It maintains a very strict level of user verification and integration with an official Telegram account to provide real-time updates to users. Various cryptocurrencies such as Bitcoin and Monero can be used to make purchases. Security researchers have been monitoring forums within the cybercriminal underworld to investigate the leading markets operating in 2024.
Store funds in wallets you control, avoid market-hosted wallets, double-check payment addresses, and consider using privacy-focused coins or mixing services to reduce traceability. Following these simple rules prevents data leaks, protects sensitive instructions, and adds a strong layer of anonymity to your transactions. Encryption may seem complex at first, but it is essential for maintaining trust and security on darknet platforms. Outdated browsers, wallets, or VPN apps often contain vulnerabilities that attackers can exploit. At the same time, avoid unnecessary downloads or opening files from unknown sources — many contain hidden malware. Staying cautious with software and limiting what you expose yourself to are critical steps in darknet market safety.

- Marcus is enough of a winner to earn both darknet stock market admiration and enthusiastic applause.
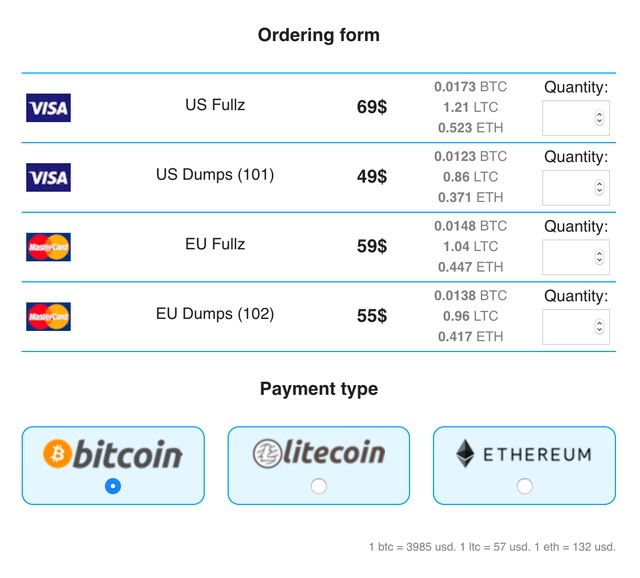
- You can pay through Monera and Bitcoin using the escrow system or the traditional market account after making a purchase on this shop.
- Additionally, by understanding how certain companies’ stocks move, traders can use their insights to trade in a more informed manner.
- Freshtools is a unique marketplace in that it does not only provide the stolen data, but it allows criminals to purchase MaaS which can cause further damage to the victims.
- Kraken Market also captured the largest share of transfers potentially sent for the purpose of obfuscating funds, as well as buying illegal products.
- Your account must be older than 4 days, and have more than 20 post and 10 comment karma to contribute.
Criminals now purchase ready-to-use malware kits, phishing templates, and ransomware programs. These tools come with user manuals and customer support, enabling even non-technical actors to conduct complex cyberattacks. Monero has emerged as the preferred currency for privacy-conscious traders.
Darknet Drugs
Multiple markets emerged to fill the void and, in doing so, created a thriving ecosystem profiting from stolen personal data. Dark markets, as well as various other services within darknets, are hosted as ‘hidden services’. This means that the servers providing these services are only accessible via Tor and do not have a public IP address or domain name. Hidden services can operate while keeping the physical location of the server hidden, which makes tracking and shutting them down considerably more challenging.
No, black market websites operate illegally and pose high risks of scams, fraud, and law enforcement action. Now, thanks to the scrutiny of one team of crypto crime researchers and Telegram’s ban hammer, it’s gone. Telegram channels, encrypted messaging apps, and invite-only forums support additional layers of communication and product distribution. Vendors advertise products through these channels and redirect buyers to secure purchasing portals.
Below are the best marketplaces on the dark net that we hand-picked after going through multiple shops and doing extensive research. The browser uses onion routing technology to route the internet traffic through multiple relay nodes that provide layered encryption. The layers of encryption hide your data and activity from snooping eyes. We are committed to providingupdated, quality and reliable information. You need to be security and anonymity-conscious while accessing these markets, and the process of doing so begins much before you type the URL for any of these markets on your browser.



