People use these platforms to sell illegal items, such as drugs, weapons, hacking services, stolen goods, and illegal services. By nature, the deep web is the part of the internet that offers more data than the surface web. However, you will not see it unless you know the IP address or URL to access the server and have the login information needed to log in. The benefit of a reliable VPN is that it runs on a network of servers designed to give you fast speeds. This means you can gain online privacy while still engaging in activities like HD streaming, gaming, torrenting, etc. Below, we’ve included an explanation of the deep and dark web and their differences.
- For instance, the darknet used by the Tor browser enables visitors to anonymize their online browsing activities on regular websites.
- Multi-Factor Authentication (MFA) is an extra layer of security you can enable on your accounts.
- All sites on the dark web end with “.onion,” as opposed to “.com” or “.org” commonly seen on the surface web.
- It is also advisable for users to look for phishing scams, where criminals share communications that seemingly originate from a reputable source.
- According to Dataprot, a rough estimate is that the surface web makes up only 5% of the internet and the rest is made up of the deep web.
- Even though the dark web is not for the average user, it has some good use cases.
Unlike the deep web vs dark web that encompass such secrecy or illegality, this surface web is totally safe to be used daily as well as it falls under more familiar laws and regulations. Hence, while the face of the internet remains the surface web, the deep and dark web are the hidden layers of the internet that require caution and understanding to traverse. Perhaps the most notorious of the dark web sectors, it is indeed infamous for hosting illicit content, which contains marketplaces trading everything from drugs and weapons to stolen data. Also contained within it are forums for discussion that include everything from hacking services to human trafficking.
Web Hosting Company Increases Security Team Bandwidth With Up To 80% Decrease In Threat Research Times
Cyber threat intelligence (CTI) helps organizations predict, understand, and defend against cyber threats, enabling proactive protection and reducing the impact of attacks. The Deep Web consists of countless legitimate applications, such as research or retrieval of personal medical records, or corporate management of data. Researchers generally use databases like JSTOR for articles, while healthcare providers maintain private information regarding patients in secure systems. Many organizations employ the Deep Web for secure data storage and communication. In this way, the Deep Web is a constituent part of today’s Internet usage.
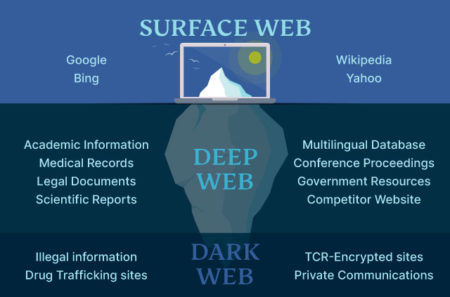
The deep web refers to parts of the internet that are not indexed by search engines like Google. This includes private databases, social networks, encrypted networks, and the dark web. The deep web consists of many different types of content and websites.
Securelist
The deep web is the internet portion that cannot be indexed by web search engines, such as Google or Bing. In fact, it includes a very large part of the internet which can only be accessed if one has particular information or credentials about accessing it. Databases are some of the significant parts of the deep web which include academic resources, medical records, and legal documents. Such databases contain highly valuable information so far lacking in most research and professional work while being inaccessible to the public. The dark web’s anonymity draws users who need private communication, want to share sensitive information, or seek access to content censored in certain regions. But while it can support legitimate uses such as whistleblowing or journalistic sources, it’s also a hub for illegal activity.

Exposure To Harmful And Illegal Activities
A good VPN like PureVPN establishes a strong connection and hides your identity to make browsing secure since the risk of dark web access is high, as most people use it for criminal activity. You will need Tor as a web browser to access the content on the dark web. It is a common misconception that the deep web is illegal, whereas many government organizations, authorities, and channels use this technology to hide their confidential data. Most of the content online sits on the Deep Web, which is not accessible via search engines, like the world wide web is. That is because the Deep Web hosts information that is private for a range of reasons, mainly security and privacy related.
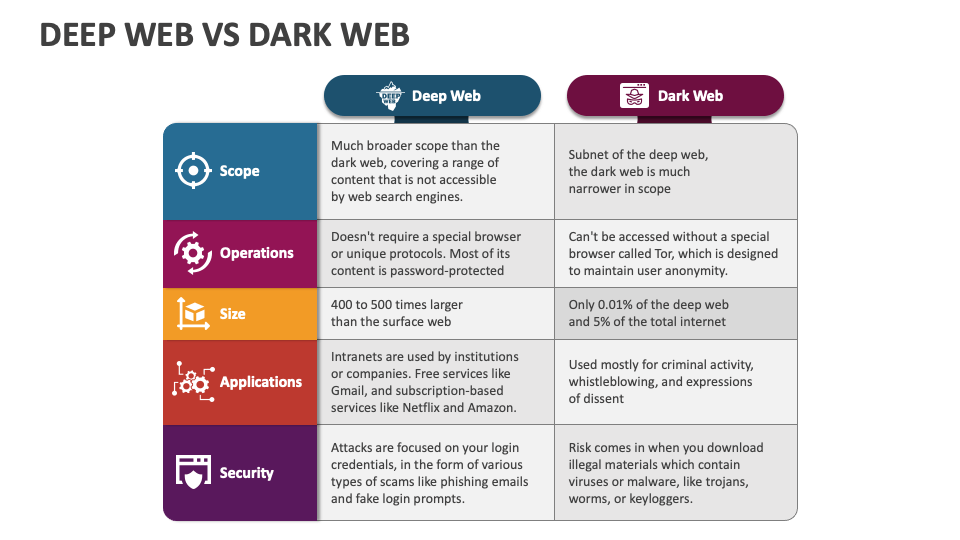
Differences Between The Deep Web And The Dark Web
If you’re taking a Cyber security training and placement course, grasping the difference between these two layers is crucial for threat detection, data protection, and ethical hacking. The key difference between the deep web and a dark web is that they both are different from the surface internet and cannot be accessed for general purposes. However, the deep web requires authorization and the dark web requires specific sets of tools and software for decryption.
- Being on the internet can compromise your security; you must use a barrier to keep yourself safe, whether on the deep or dark web.
- This makes Dark Web sites a rich source of threat intelligence for organizations; however, the design of the Dark Web can make this information difficult to find.
- While the Dark Web does host illegal content, it also provides refuge to whistleblowers, journalists, and activists under threat from authoritarian regimes.
- The surface web is the most popular and accessible part of the Internet, involving all websites indexed through traditional search engines like Google and Bing.
- On the other hand, the dark web welcomes more distinct groups of users, like criminals, whistleblowers, or political dissidents, who leverage off the anonymity the dark web provides.
Legal Implications
The dark web is home to stolen identities, credit cards, national IDs, passports, etc. And since we can’t access every dark web onion site to see if our own credentials are up for sale, we have some monitoring tools embedded within NordVPN and 1Password. Consequently, using Tor (to visit the dark web) is something an average internet user does not do.
Navigating The Twists And Turns Of The Digital Cosmos: Penetrating The Multifaceted Depths Of The Unseen Internet

It even has a dark web monitor to notify you in case your data gets leaked on the dark web. Another factor to note is that while your traffic is encrypted several times, it’s not encrypted as it exits the last server in the chain. Law enforcement officials in some countries have been found to run or seize exit nodes to monitor dark web traffic. If your traffic passes through a compromised node, the authorities can see your real IP address and potentially trace the activity back to you.
Now that you know what the deep and dark web are, seeing their differences may be a bit easier. But just to make sure you have a clear picture, we’ve outlined them for you below. The dark web’s layered encryption and routing methods make it extremely difficult for security teams to identify who is behind malicious activities. Discover the key differences between the Dark Web and Deep Web, their uses and risks to businesses. A high-quality Cybersecurity training and placement program can empower you with the tools, techniques, and confidence to thrive in this hidden digital terrain.
Understanding how these parts of the internet work helps you protect your security and privacy as you navigate them. Drugs, death, and depravity probably come to mind whenever you hear about the dark web. You might find yourself conflating the two terms, with the assumption that both the dark web and the deep web are the same place for illegal and generally shady activities.
PRIVACY ALERT: Websites You Visit Can Find Out Who You Are
The principle of ‘onion routing’, which underpins TOR, was developed by the researchers Paul Syverson, Michael G. Reed and David Goldschlag at the United States Naval Research Laboratory in the 1990’s. The very first version of Tor, named ‘The Onion Routing Project’ or simply TOR Project, was developed by Roger Dingledine and Nick Mathewson. Since this turmoil, management and oversight of the software powering the largest dark web network has been fairly stable and consistent.
Deep Web Vs Dark Web: Key Differences
The security implications of the surface web differ significantly from its hidden counterparts. From a regulatory perspective, the Deep Web aligns with mandates like GDPR, which demand controlled data environments. Businesses benefit from this, ensuring proprietary information remains exclusive. By volume, the deep web constitutes approximately 90% of all internet content (according to Google’s documentation mentioned above). Furthermore, 31 new ransomware groups were discovered in 2024 (a 30% year-over-year rise in active ransomware groups).
Dark Web Vs Deep Web Monitoring: What Security Teams Need To Know
Dissidents, free speech activists, whistleblowers helping investigative journalists, and many more people use the dark web to evade persecution and communicate anonymously online. Secure and affordable tools exist for that purpose, but some prefer a more radical approach. If something cannot be found, even if it can be opened, then it too belongs to the deep web.