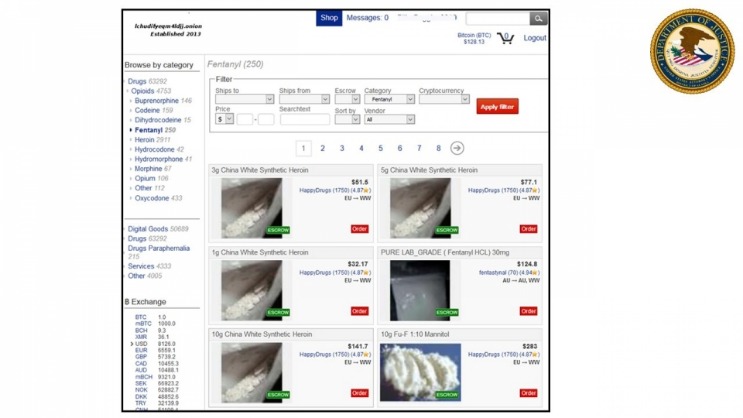
This use of cryptocurrency makes transactions fast and secure, and it supports the overall goal of privacy on the dark web. The key differences between dark web markets and regular online stores are clear. Regular stores are public, with visible ads and a standard payment process.
- Following these simple rules prevents data leaks, protects sensitive instructions, and adds a strong layer of anonymity to your transactions.
- In May 2024, Ticketmaster faced a significant data breach affecting millions of customers.
- This diversification reduces dependence on centralized markets and increases the resilience of criminal networks.
- The use of cryptocurrencies such as Bitcoin and Monero remains central to these platforms, ensuring anonymous transactions and reducing the risk of financial tracking.
- These breaches can result in regulatory penalties for failing to comply with frameworks such as GDPR or HIPAA.
Digital forensics helps in tracing digital footprints back to their sources. After all, criminals are getting more creative and professional by the day, running their operations like businesses with customer service and even reviews. The growing shift toward more sophisticated and user-friendly criminal organizations is quickly becoming a real headache for cybersecurity firms. In addition to its emphasis on stolen credentials, 2easy Market offers a variety of cybercrime tools, such as hacking services, exploit kits, and other resources for conducting cyberattacks. The market frequently makes headlines for releasing massive troves of stolen data, often as a way to advertise its services. The Russian Market has been around since 2019 and is one of the more prominent dark web marketplaces.
Global law enforcement agencies face mounting challenges in tracking and dismantling dark web operations. In 2025, authorities have increased efforts to identify illicit transactions, monitor suspicious wallet activities, and take down infrastructure supporting criminal trade. However, the rapid evolution of these marketplaces continues to outpace many of these initiatives. Telegram channels, encrypted messaging apps, and invite-only forums support additional layers of communication and product distribution. Vendors advertise products through these channels and redirect buyers to secure purchasing portals.
Conclusion For Our Research In Marketplaces
In 2025, only a few markets stand out for their security, reliability, and vendor quality. Dark markets often employ end-to-end encryption for communication between buyers and sellers, enhancing security and privacy. This encryption ensures that messages cannot be intercepted and read by third parties, including law enforcement. The use of digital signatures can also help verify the authenticity of users and transactions. Transactions within dark markets predominantly involve cryptocurrencies like Bitcoin, Monero, or Ethereum.

The Dangers Of Darknet Marketplaces
There’s high exposure to malware and cybersecurity threats that can steal your personal information. Law enforcement agencies actively monitor these markets and can track users despite anonymity measures. You risk legal consequences if caught participating in illegal transactions. Financial fraud is common, and you have no recourse if transactions go wrong since these markets operate outside legal frameworks.

Illegal Substances And Weapons
In this blog, we’ll reveal how the dark web is being used in 2025, which countries are driving curiosity, and what the latest data reveals about access trends. We do not engage with darknet markets; our mission is exclusively dedicated to providing information for research and educational purposes. As the darknet continues to grow, its markets are expected to adopt even more sophisticated tools for secure trading, further enhancing the user experience and solidifying their role in modern commerce. Forums and magazines play a crucial role in keeping users informed about new market links and updates. Platforms like Dread and Darknet Live provide real-time discussions, vendor reviews, and security tips, ensuring users can navigate the darknet safely and efficiently.
Talk To A Dark Web Intelligence Expert
The dark web market changes all the time, but some dark web marketplaces have made a name for themselves as the biggest and busiest spots. These sites attract thousands of users every day, offering all kinds of illegal goods that keep the underground trade going. Most buyers and sellers use the Tor network, which hides IP addresses and locations. Doing so makes it harder for authorities to identify who’s behind a purchase or a listing. Vendors often build up reputations through ratings and reviews, just like sellers on mainstream platforms.
Cyble Titan Endpoint Security
Interestingly, India has also climbed into the top 10, with more than 113k daily users, proving that curiosity about the dark web isn’t limited to the West anymore. Since the disappearance of Evolution and Agora, several smaller markets have appeared, with some approaching the size of Evolution or Agora at their peak, though no one market leader has emerged. This shows that while the dark web gets all the attention, it’s far from the internet’s biggest problem. To use social login you have to agree with the storage and handling of your data by this website. Monero’s privacy beats Bitcoin’s traceability—BTC usage dropped 40% since 2023 due to tracking risks.
- You can access it for legitimate purposes like whistleblowing and freedom of expression.
- This means that the servers providing these services are only accessible via Tor and do not have a public IP address or domain name.
- While it offers anonymity for legitimate purposes, it is also a haven for cybercriminals.
- Other platforms concentrate solely on narcotics, counterfeit items, or stolen digital identities.
- Quality and validity of the data it provides justify its higher cost over other marketplaces.
These platforms also often have built-in encryption for communications and transactions, making it hard for law enforcement to track down the individuals involved. The cloak of secrecy provided here is what keeps these dark web marketplaces bustling with illegal activities, posing a significant challenge for cybersecurity experts and authorities worldwide. Dark markets provide a one-stop-shop for cybercriminals, offering a wide range of services such as hacking tools, stolen data, ransomware, and Distributed-Denial-of-Service (DDoS) attacks for hire.
Exploring The Use Cases Of Darknets & Dark Markets
Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering everything from drugs to stolen data. The Tor project gained notoriety for enabling illegal marketplaces like the Silk Road, a black market taken down by the FBI in 2013—and countless cybercriminal service providers ever since. Still, the Tor dark web browser also remains a vital tool for privacy-conscious users. Businesses can use deep and dark web monitoring tools to keep track of stolen credentials or mentions of their brand to protect against cyberattacks. While the dark web is not inherently illegal, it does host a range of illegal content, hidden services, and illicit activities.
These innovations challenge law enforcement and raise new questions about regulation and control. Venture deeper into the underbelly of the dark web, where bustling marketplaces hum with activity and cryptic figures pull the strings. This article unveils the prominent players, explores the vendor ecosystem, and delves into the security measures employed in this digital Wild West. There are many initiatives and programs aimed at teaching the public about the risks and how to stay safe, such as cybersecurity workshops and online courses designed to educate and inform. These efforts help folks learn how to secure their personal information, recognize suspicious activity, and take preventative measures. It’s also super important to train employees to spot phishing attempts and other cyber threats.

Businesses must prioritize cybersecurity by implementing Dark Web scanning tools, strengthening access controls, and educating employees about emerging threats. Identifying security vulnerabilities before cybercriminals exploit them is essential for maintaining operational integrity. Although it can be a bastion for privacy, the presence of dangerous products and services – from hacking tools to weapons – raises ethical concerns about the role of these markets in perpetuating harm. The dark web is a part of the internet that isn’t indexed by search engines. You’ve no doubt heard talk of the “dark web” as a hotbed of criminal activity — and it is. Researchers Daniel Moore and Thomas Rid of King’s College in London classified the contents of 2,723 live dark web sites over a five-week period in 2015 and found that 57% host illicit material.
Companies today face constant threats of data theft, intellectual property leaks, and other dangers that originate from the dark web. At KELA, we help you identify and mitigate risks by providing actionable intelligence from the darknet. Our solutions empower you to monitor illicit darknet marketplaces and track emerging threats, ensuring you can take proactive measures to protect your organization and reputation. Markets like AlphaBay and Hansa adopted stronger encryption and expanded offerings to include hacking tools and stolen data. However, these platforms often faced law enforcement takedowns, technical issues, or exit scams, where operators vanished with user funds.

While Tor anonymizes your connection, a VPN adds an extra layer of security by hiding Tor usage from your internet provider and reducing traceability. While Tor provides anonymity, combining it with a reliable VPN adds another layer of protection. A VPN hides your real IP address from your Internet Service Provider and ensures your Tor usage is not easily detected.
Get News, Insights & Intelligence Straight To Your Inbox
Popular darknet market lists and links help users navigate the best options, ensuring access to verified darknet sites and marketplaces. The darknet drug market continues to grow, with 2025 projections indicating expanded availability and improved user experience. Darknet magazines and forums provide updates on new markets, onion addresses, and URLs, facilitating seamless transactions. Cryptomarkets on the darknet remain a key resource for those seeking privacy and efficiency in online trade. This chapter studies the market places, which are operating in the Dark Web.
By mid-2025, several high-profile marketplaces were either hacked, exit scammed, or seized. Others were taken down in joint operations by cybercrime units across Europe and North America, continuing the trend of global coordination seen in past takedowns like Operation Disruptor. Governments have become more efficient, using AI tools and blockchain analysis to deanonymize users, track crypto flows, and target market infrastructure.



