
The creators assert that because their technique is so strong, even malware with root access could not determine the machine’s IP address. However, there are some significant variances in the background despite the similarities. For example, Whonix’s virtual workstation machine connects to the internal virtual LAN. It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address.

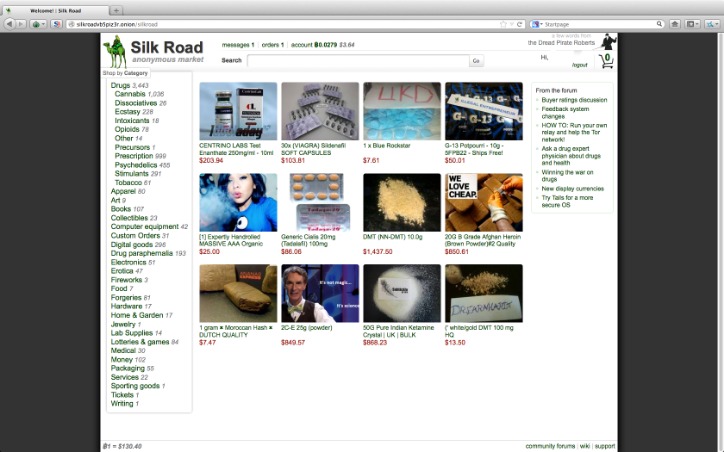
It uses PGP encryption, two-factor authentication, and OPTP authentication to ensure users’ security. Mega Market is a new yet popular shop on the dark web that reached a skyrocketing reputation after the closure of the Hydra market. It allows you to buy and sell a wide range of products and services with a good user experience. This site supports PGP encryption and two-factor authentication features. DarkFox Market is the largest dark web shop selling various products and attracting more vendors and users. It is a wallet-based shop, meaning you must first deposit bitcoins into your wallet before purchasing any goods and services.
BBC News /tamil தமிழ்
They belong to the Tor network, which hides both the user’s identity and the server’s location. Instead of short, simple names, these domains appear as long strings of random letters and numbers ending in .onion. To open them, you need the Tor Browser, which routes traffic through multiple encrypted relays. This is a categorized list of notable onion services (formerly, hidden services)1 accessible through the Tor anonymity network. Defunct services and those accessed by deprecated V2 addresses are marked. Using TAILS is yet another security measure that protects your online identity on the dark web.
Tor And The Onion Browser
You need to register first to purchase products from this marketplace. The marketplace has a pleasant, user-friendly interface built from the ground up. Its interface makes it easy to identify clone websites and ensures that users always use the authentic site. When you’re dealing with sensitive information, nothing feels truly anonymous or private.
If I’m A Noob And Want To Explore Onion Sites, What Should I Know?
If you ever decide to explore the dark web, protecting your identity is crucial. Most people start by using the Tor Browser, which hides your IP address. These sites cater to cybercriminals seeking valuable data, such as credit card numbers, login credentials, and personal information. Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down. Here are some things to keep in mind while browsing your favorite dark web websites.
- This is especially important for individuals in regions where press freedom is restricted or where government surveillance poses risks to journalists and activists.
- Libraries, forums, and archives give students and researchers access to material often locked behind paywalls.
- Torch is funded primarily through advertising—purchased in BTC, of course—which is why you’ll find the front page blanketed with old-school banner ads of dubious origins.
- Using an anonymized browser does not make these actions right.
- These systems route all traffic through Tor by design and erase traces when shut down.
Subscribe To Our Newsletter!
With 256-bit AES encryption, this platform enforces its two-fold service of secure messaging and zero logs of your activity. In addition, you can connect your Keybase account with X, GitHub, or Reddit to let people easily trust that they are talking to the actual person. Also, the platform has a feature of automatic deletion of messages – set a timer and they will be deleted after a set period. In addition, Haystak offers a premium plan that allows deeper search, email alerts, and access to historical content.
Share This Article
For ordinary citizens, onion services offer a way to discuss sensitive topics without fear. Communities focused on digital rights, minority issues, or political debate thrive on the hidden web because members feel safer sharing their views. Even in freer societies, people value the chance to express opinions without linking them to real-world identities. Whistleblowers often rely on SecureDrop, a platform designed to let them share sensitive documents with journalists without exposing their identity. Normal URLs rely on centralized DNS systems, while onion addresses use decentralized routing within Tor.
Easy Steps To Access Dark Web On Your Phone Safely In 2024
Think of Tor as a regular browser like Firefox, Google, or Safari. The only difference is that it passes your traffic through random nodes before reaching the destination. This means your activities cannot be traced or your browser history exposed.

No info is available on the explored institutions or how these sections can be accessed. I think it’s safe to say that these are unsanctioned exploits, all the more reason to boast them on the dark web. I have to admit to having a soft spot for Tunnels, an onion website about underground “urban” exploration. Apart from having that “As above, so below” vibe, Tunnels is a great source of info for users who are into dark urban history.
It serves the same purpose as ProPublica – facilitating access in countries where it may otherwise be restricted. From Flickr to Facebook posthaste – that would be an accurate description of Dark Lair, an image hosting platform turned social media. Dark Lair allows you to post comments, share music, upload photos, message your dark web ‘friends’, and everything in between. In this sequel, I’m going to show you some of the not-so-clear-web’s hidden Easter eggs and how to get there. So, without delay, let’s step into the onion patch aka the best 20 dark web websites.
It’s a popular choice for users worried about online surveillance and data collection. To make its journalism more accessible to readers around the world, the New York Times launched its onion service in 2017. Everyday users rely on hidden services to avoid tracking or to shield communications. In restrictive countries, this anonymity can enable free expression. Some users also reuse their personal accounts or email addresses inside Tor.
- These spaces provide both information and community support.
- For a deeper look at the safest tools to navigate hidden services, see this guide to the best dark web search engines that help users find reliable onion links.
- Your account must be older than 4 days, and have more than 20 post and 10 comment karma to contribute.
- To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web.
- There are often copious amounts of how-to articles, software exploits, and hacked credentials for sale.
Best Free VPNs For The Dark Web In 2025: Secure & Fast
You can access almost any published paper that would have otherwise been hidden behind a paywall. The developers of ProtonMail recommend using the Tor browser to visit the dark web version of the service. This ensures greater security and privacy, making it much more difficult for snoopers to get in. With ZeroBin, you can easily exchange encrypted messages within the dark web.



